10 Best Breach and Attack Simulation (BAS) software
Destruction and attack simulation is an advanced computer security testing method. These simulations identify vulnerabilities in security environments by mimicking attack paths and techniques that malicious actors might use. In this sense, breach and attack simulation is like a continuous automated penetration test.
Breach and attack simulations are a new way to test IT security efforts by simulating real-world attacks to determine whether an organization’s various security measures are truly serving their purpose.
Top 10 Software
What is the Best Breach and Attack Simulation (BAS) software ?
Here’s a list of the best Breach and Attack Simulation (BAS) software :
1. SOPHOS
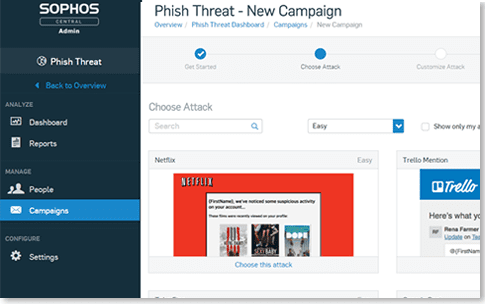
Sophos PhishThreat gives you the flexibility and adaptability your organization needs to foster a positive culture of security awareness. It trains and tests your end users with automated attack simulations, quality security awareness training, and actionable reporting metrics.With this software, you can simulate hundreds of realistic and challenging phishing attacks with just a few clicks.
SophosLabs’ global analysts monitor millions of emails, URLs, files and other data points every day for the latest threats. This constant flow of information ensures that user training covers current phishing tactics, and socially relevant attack simulation templates cover a variety of scenarios from novice to expert, all translated into nine languages.Take advantage of their collection of 30+ security awareness training modules covering security and compliance topics.
Sophos Phish Threat integrates testing and training into an easy-to-use campaign that provides automated on-site training to staff when needed.The Phishing Threat Dashboard provides at-a-glance user breach activity results and allows you to measure the overall risk level of your entire user group using real-time awareness factor data, including: top activity results, captured organizational trends for employees and journalists, and overall user capture up.
Sophos Synchronized Security connects phishing threats to Sophos Email to identify people who have been warned or blocked from accessing websites based on risk profile. You can then seamlessly enroll them in targeted phishing simulations and training to increase awareness and reduce the risk of attack.
2. RANDORI

Randori is one of the Best Breach and Attack Simulation (BAS) software, is an attack surface management solution that automatically scans services, IPS, domains, networks, and more for ransom ware and other attacks. Randori’s black-box approach discovers, identifies, and maps your external attack surface. 100% cloud-based, with no agents or appliances to install, Randori immediately begins discovering targets, services, IPs, domains, networks, hostnames, and other artifacts that attackers see when targeting your organization. All you need is an email to get started. It provides a unified view of your organization’s most important goals.
Their patent-pending Target Temptation technology puts each target in context and goes beyond vulnerability assessment to give you a more comprehensive assessment of real-world risk.
With this software you can:
- Uncover shadow IT and find forgotten assets, blind spots, and process flaws that allow attackers to bypass your defenses.
- Stop ransomware before it strikes by hardening and reducing your attack surface with Randori’s leading Attack Surface Management platform.
- Test the real-world effectiveness of your SIEM, EDR, SOAR, threat intelligence, and MDR partners
3. DATTO

With Datto SaaS Defense, MSPs can proactively defend against malware, Business Email Compromise (BEC) and phishing attacks targeting Microsoft Exchange, OneDrive, SharePoint and Teams.
The main features of Datto are:
First encounter detection: Datto SaaS Defense is an advanced threat protection solution that detects zero-day threats the first time they are encountered, not days later.
Protection beyond email security : Proactively protect your customers’ Microsoft 365 data in OneDrive, SharePoint, and Teams.
MSP’s Security Package: Your comprehensive security solution will help you win new customers and grow market share without increasing headcount or investing in security training.
With this software you can:
Defense Unknown: Datto SaaS Defense differs from traditional email security solutions, which rely on data from previously detected cyber threats.
Identify unknown threats : Instead of looking for known security threats, SaaS Defense’s data-agnostic technology detects unknown threats that other solutions miss by analyzing the makeup of secure emails, chats, or documents.
Minimize detection time: SaaS Defense does not rely on third-party software, minimizing the time it takes to detect intruders.
Protect data from zero-day threats: Inefficient native SaaS application recovery capabilities mean your customers are vulnerable to data loss.
4. PICUS

Picus is a complete security verification platform that automatically verifies your organization’s cybersecurity posture and gains actionable insights to build 24/7 resiliency. It measures security effectiveness, quickly evaluates controls, automatically and consistently identifies gaps, and immediately applies selected mitigation recommendations for security verification, hardening, and mitigation purposes.
The platform builds on an extensive threat library curated by Picus Labs and extensive risk mitigation recommendations from the Picus Technology Alliance network.
This tool allows you to:
- Gain a better understanding of your attack surface and understand how attackers may target critical assets.
- Continuously measure the effectiveness of security controls and processes to assess your threat readiness at any time.
- Get the data you need to focus remediation and mitigation efforts on areas that will have the greatest security impact.
- Get actionable insights to address gaps more swiftly and maximize the value of existing security investments.
5. AVALANCE
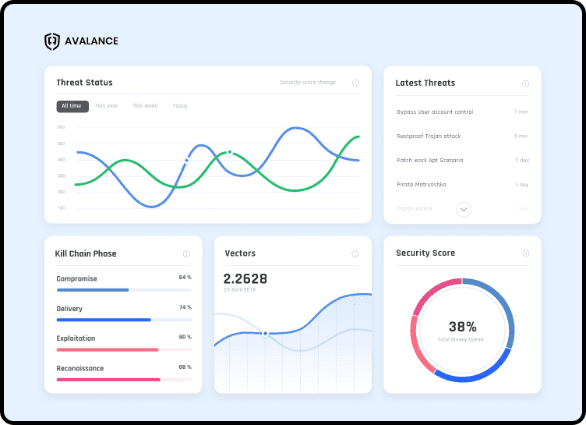
Using examples of emerging threats,Avalance continually challenges your readiness for emerging threats, identifies strengths and weaknesses of security measures in real time, and helps you get the most from your security investments. It identifies security vulnerabilities in real time and takes action within minutes, and Avalanche Mitigation Guide provides an interactive dashboard that presents the big picture with objective metrics listing the vulnerabilities found.
For vulnerabilities discovered during our assessment, Avalance provides vendor-specific fix signatures and creates a priority list.
Key advantages of the platform:
- Inform you of current security effectiveness, including any emerging threats.
- Helps you prioritize security resources where they are needed most.
- Send alerts for conditions that increase security risks.
- Allows you to demonstrate the effectiveness of individual systems or the security posture provided by a security stack.
- It ships with an open source remediation know-how that can be consumed by your security technologies.
6. ATTACKIQ
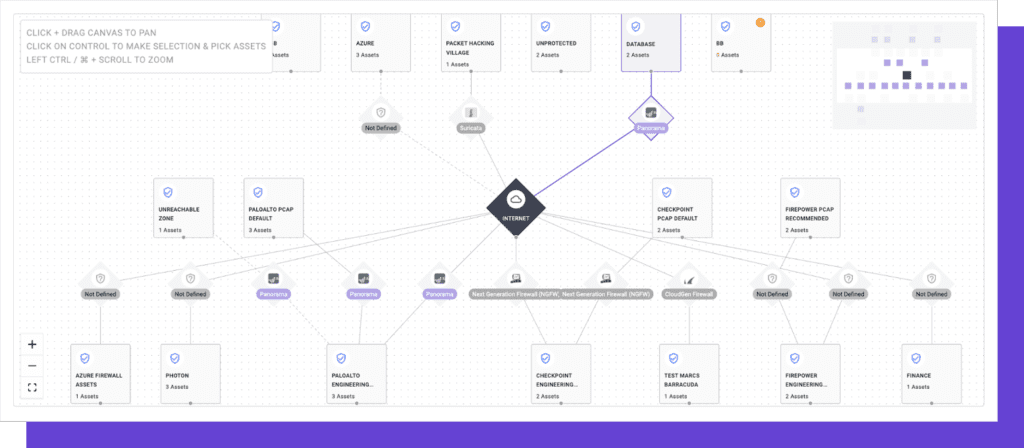
AttackIQ‘s Security optimization platforms realistically simulate adversaries to test your security programs and generate real-time performance data to improve your security posture.
It has:
Dashboard: Consolidates the results of multiple assessments and provides quick access to insights by MITER ATT&CK, security controls, and asset groups related to specific adversary behavior.
Rating: Allows you to quickly run scenarios through the entire kill chain. Continuous awareness of your defenses can be arranged.
Testing: is the component of evaluation that assesses the performance of your defense against a multifaceted enemy campaign against a specific objective.
Scenes: Your library contains thousands of scenes, or you can create your own to capture specific TTPs.
Mitigation: Generate explicit recommendations to help users quickly achieve a secure state.
Preconfigured Agents: Instantly communicate with the platform without additional configuration, etc.
The software delivers:
- Features you care about most, from endpoint discovery to segmentation.
- Detailed control detection and prevention information to improve effectiveness.
- Benefit from extensive cybersecurity community engagement through AttackIQ Academy, Purple Hats, and Informed Defenders.
- Close partnership with the MITER ATT&CK team and MITER Engenuity’s Threat Informed Defense Center.
- Clear, technology-specific remediation guidance tailored for each control.
7. CHARIOT
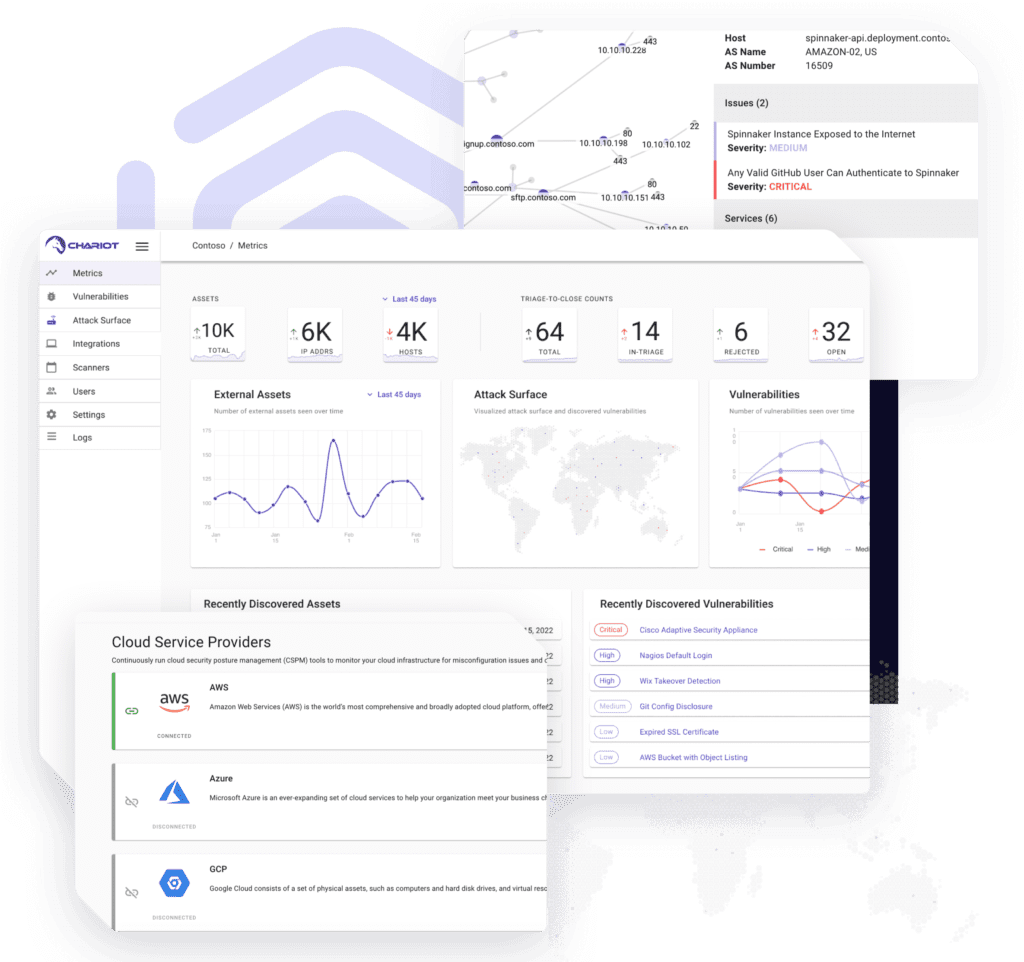
With Chariot you can defeat attackers, by partnering with the industry’s leading provider of offensive security services. It put you back on offense by combining security expertise with technology automation for continuous focus and improvement on your defensive investments.
Chariot’s main features :
Bundled with security experts: Dedicated offensive security experts are assigned to your account to assist you throughout the attack lifecycle.
Eliminate false positives: Part of their core value is to only signal when it matters and guarantee there are no false positives.
Adding an attacker’s perspective: The platform was quick to implement new technologies into the Chariot platform long before pure product companies even realized that new attack vectors existed.
Advanced Asset Detection:Through integrations with cloud providers, source control managers, container registries, workloads and ci/cd pipelines, Chariot provides continuous, comprehensive and contextual asset discovery.
8. ELASTICITO :
Elasticito combines the latest cutting-edge automation technologies with the skills and experience of cyber experts to provide clients with unparalleled visibility and control over the cyber risks their organizations face.
it features :
Test: Your entire security infrastructure to determine where your security is functioning, where there are gaps, and which issues have the highest priority to fix based on potential damage to your business.
Assess: Your Business’ Cyber Risks, provides you with the information you need to protect your business from cyber-attacks and raises your awareness of the risks posed by third parties.
Recommendations: How to reduce cyber risk by getting a clear picture of your security posture, how you compare to your competitors, and where you stand with relevant compliance standards and regulations.
Engineers: Use the MITER ATT&CK framework to provide protection, detection and response solutions for the entire asset lifecycle.
Automation: Provides continuous assessment and testing of your entire security infrastructure.
9. Exploit Pack
Exploit Pack is a cross-platform exploit framework with zero-day exploits and 39,000+ exploits, post-exploitation modules, undetectable and ready for your next target. The platform is intended to be used by hands-on security professionals to support their testing process.Exploit Pack replicates real attack scenarios and detects potential threats in your security environment before they are hacked. Developed by a team of experienced software developers, it leverages Composer to automate the process so security professionals can focus on what really matters.
Uncover threats and reduce the attack surface, exploit Pack’s advanced graphical user interface makes it easy to use and enables rapid reconfiguration to adapt exploit code, post-exploitation modules, and utilities to changing threats.Access our current zero-day exploits, as new vulnerabilities are discovered in our labs, you will receive these new exploit codes as an update in your Exploit Pack.
Make use of Exploit Pack post-exploitation modules to improve the resilience and check the effectiveness of your current config of EDR/Antivirus and NGFW.
10. FourCore Attack

FourCore ATTACK is a Platforms designed to execute complex attack scenarios such as malware or attackers. BAS solutions allow you to test the effectiveness of your security controls. Extensive cybersecurity knowledge and expertise are not required.FourCore ATTACK assesses control over the attack surface. You can run simulations on endpoints protected by EDR and EPP solutions. Evaluate the effectiveness of SIEM rules. See if your firewall can detect and block malicious payloads on your network. Test whether your phishing solution can block malicious emails.
The platform can:
- Identify vulnerabilities by mimicking real attack paths used by threat actors.
- Generate real-world attack telemetry and your security baseline to reduce detection and response times.
- Simulate sophisticated threats and sophisticated TTPs from phishing to ransomware.
- Find out if you’re getting the promised value from your security investments against real-world attacks.
- Verify the possible impact of an attackerin your company in a safe way.
It has more than 500 different techniques and procedures to validate the effectiveness of SIEM, DLP and every other security control.
Conclusion :
Despite the challenges, properties that install building automation experience immediate improvements for residents and staff. Thanks to IoT-powered systems, owners will see a return on investment faster than ever, sometimes in as little as a year. With new smart building software, building automation systems become the platform for future technologies and the means to future-proof your buildings.





