10 Best Encryption Software
Encryption is all about scrambling data to prevent unauthorized parties from being able to understand what is contained in the information. It takes regular text and converts it into an incomprehensible series of letters, numbers, and symbols. Some kind of cryptographic key is needed to both encrypt and decrypt the data. Such complexity is normally shielded from users. All they need is the right way to access the data.Hackers, on the other hand, need to crack the code to reveal what the data contains. You may have seen passwords getting longer and more complex in recent times. This stems from how easily cybercriminals can figure out passwords and decrypt data or gain access to systems using a brute-force approach. Encryption algorithms and technologies, therefore, have to stay ahead of the pace of the brute force technology used by hackers.
There are far too many encryption tools to cover them all here. This list contains both traditional encryption tools that offer file encryption for data in motion .
Top 10 Software
1.Progress MOVEit
Progress MOVEit offers a range of solutions to help companies:
Securely transfer files between applications, internal users, external customers or business partners.Automate and administer tasks without advanced programming.Consolidate costs and management while establishing a documented audit trail.Meet internal and external compliance requirements including HIPAA, SOX, GDPR, FINRA, BASEL, PCI and others.
2.WatchGuard
WatchGuard Network Security is a network security and firewall software. WatchGuard has been in the cyber security technology space for over 20 years. The vendor sees itself as a pioneer in the space, and aims to deliver easy-to-deploy and easy-to-manage solutions. WatchGuard offer a comprehensive advanced network security platform that puts IT security professionals back in charge of their network with widely deployable, enterprise-grade security and threat visibility tools suitable for an organization, regardless of budget, size or complexity. In addition to network security, WatchGuard includes secure Wi-Fi, multi-factor authentication, and network intelligence products and services. The vendor says this is important because the cyber security landscape is constantly evolving, and new threats emerge each day. WatchGuard’s goal is to make enterprise-grade cyber security technology accessible for every company. The vendor reports that WatchGuard serves more than 80,000 small and midsize enterprises around the globe and is headquartered in Seattle, Washington, with offices throughout North America, Europe, Asia Pacific, and Latin America.
3.Tresorit
Tresorit is a Swiss, end-to-end encrypted, zero-knowledge content collaboration platform designed to safeguard the digital valuables of individuals and organizations with the highest classification in the cloud. Unlike other public cloud vendors, Tresorit has no access to users’ files, which ensures maximum confidentiality.- Uncompromised security: Your files are protected from the moment you upload them to the cloud until they reach the intended recipient. It is technically impossible for anyone else to gain unauthorized access to your files.- Seamless and secure teamwork: Whether it’s personal data for HR documents, legal contracts, financial plans, or top-secret R&D prototypes – Tresorit provides a digital workspace where your highly sensitive documents remain safe.- Powerful control and monitoring options: Manage and oversee all users and their information and activities. Tresorit offers powerful control features so you can be sure that the right employees access the right files.
4.Virtru

Virtru makes military-grade encryption easy and affordable. We equip organizations of all sizes to take control of their data with flexible, end-to-end encryption for data flowing in and out of your business. Virtru’s tools are easy to use and integrate seamlessly with Google Workspace/Gmail and Microsoft 365/Outlook, as well as enterprise apps such as Salesforce and Zendesk. Our granular access controls, key management options, DLP rules, and persistent audit help our customers meet even the strictest privacy and compliance requirements, including ITAR, CMMC 2.0, CJIS, HIPAA, and GLBA/FTC Safeguards. Users can encrypt information with a single click, without leaving their existing workflows, because Virtru is integrated directly inside the apps they use every day. The result is fast, easy security that follows your data everywhere it moves, inside and outside of your organization.
5.BitLocker

BitLocker is a full disk encryption solution that protects your data from theft, hacking, and loss. BitLocker achieves this by encrypting the entire drive that hosts your operating system and all your data. BitLocker can work on all operating systems, drives, or devices, including portable storage devices.After BitLocker completes the data encryption, it generates a recovery key. Only those with the correct encryption key will be able to decrypt and access the encrypted files and information. Attempts to access secured data on premises or over the network will be met with either authentication prompts or error messages saying the data cannot be accessed.BitLocker provides its users with peace of mind by improving security and reducing risks of critical data loss and intrusions.
6.Kaspersky Endpoint
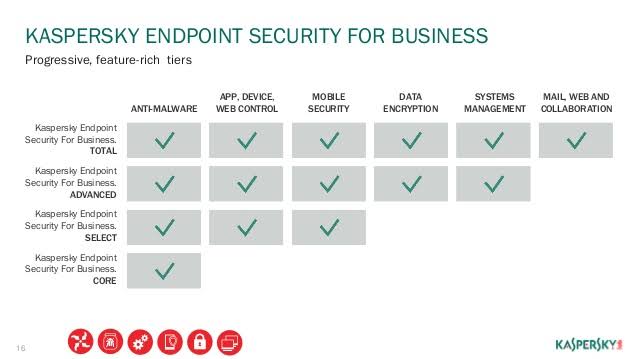
Kaspersky Endpoint Security is a multi-layered endpoint protection platform, based on true cybersecurity technologies. This tightly integrated solution combines fully scalable protection capabilities for physical, virtual and cloud-based endpoints including desktops, servers, mobile devices and embedded systems. Every endpoint can be managed through one unified console, giving you a complete security overview, no matter how extensive your infrastructure. Kaspersky Endpoint Security delivers a reliable, enterprise-ready security platform, providing data to automatically enrich your SOC. Endpoint vulnerabilities and protection are managed together through one console, improving efficiency and reducing your TCO. It protects you from ransomware, exploits and even the most advanced forms of cyberthreats. It has Easy and effective centralized web, device and application controls reduce your attack surface and help keep users safe. And FIPS 140.2 certified full disk encryption helps fully protect confidential data on stationary and mobile devices.Kaspersky Endpoint Security for Business was previously known as Kaspersky Work Space Security, Kaspersky Endpoint Security.
7.ESET PROTECT Advanced
ESET Endpoint Security provides multiple layers of protection and can detect malware before, during, and after execution. Machine learning, advanced behavioral analytics, big data and human expertise work in dynamic equilibrium to balance performance, detection and false positives.
ESET Dynamic Threat Defense provides proactive protection against zero-day threats, by executing all submitted suspicious samples in an isolated and powerful cloud sandbox environment, in order to evaluate their behavior using threat intelligence feeds, ESET’s multiple internal tools for static and dynamic analysis, and reputation data.
ESET PROTECT is a cloud-based, multifunctional remote network security management tool for ESET business security products across all operating systems. It enables one-click security deployment and gives you network visibility without the need to buy or maintain additional hardware, reducing the total cost of ownership..
8.VERY GOOD SECURITY
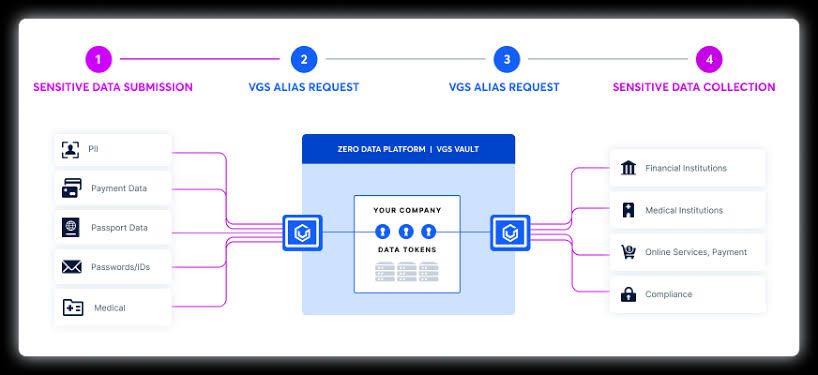
The VGS Platform protects the collection, storage and exchange of sensitive data and secures that information in a secure data vault; enabling clients to de-risk their technical environment and achieve compliance certifications like PCI DSS, faster via the VGS Zero Data™ approachThe VGS Zero Data approach allows you to operate on sensitive data without the risk and liability of touching or storing it; decoupling the value and utility of data from the associated security and compliance risks. The VGS Zero Data approach allows clients to achieve continuous PCI compliance 16x faster, at 25% the cost of a DIY approach; enabling clients to strategically deploy time and resources towards developing solutions and scaling their business.
9. New softwares.net (folder lock)

NewSoftwares LLC is committed to providing strong, effective solutions in information security to its immediate customers and long-term partners & clients. We are constantly engaged in research and development, our focus lies on how to create new and improve existing products by utilizing the latest technological standards currently available.
Provided by NewSoftwares, Folder Lock provides bullet-proof data encryption services for individuals. Furthermore, Folder Lock is an excellent choice if you are trying to add encryption to your mobile devices.This service will allow you to add encryption to any device that stores critical data.The app will protect your personal files, photos, videos, contacts, wallet cards, notes, and audio recordings stored in your handset. It also provides you with some other great security features as well.Not only do you get access to the encryption software, but you will also have the ability to set a decoy password, hacker deterrents, log unauthorized login attempts, back up all your passwords, and get notified on potential brute-force attacks.
10.hashicorp vault
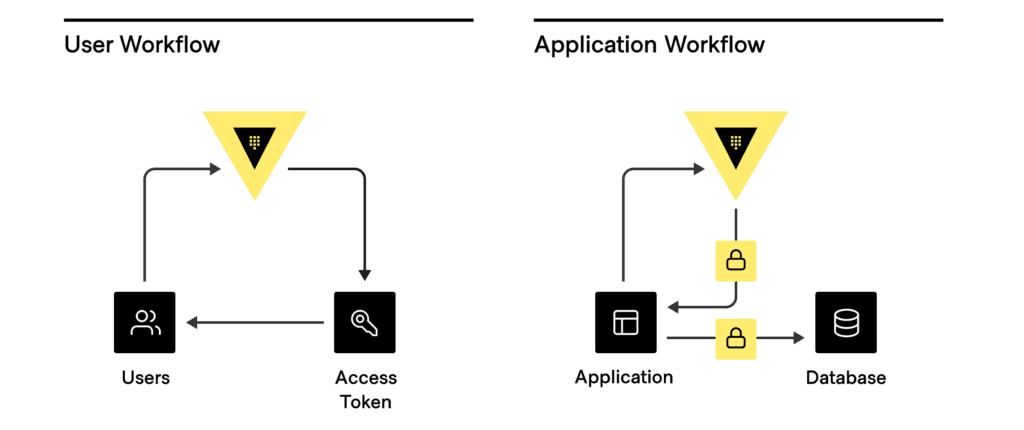
HashiCorp Vault is an identity-based secrets and encryption management system. A secret is anything that you want to tightly control access to, such as API encryption keys, passwords, and certificates. Vault provides encryption services that are gated by authentication and authorization methods. Using Vault’s UI, CLI, or HTTP API, access to secrets and other sensitive data can be securely stored and managed, tightly controlled (restricted), and auditable.
“The solution is used as a way to manage the access to different systems and servers. Basically it gives us a way to generate, store and manage the secrets (authentication) for a variety of servers and production systems. We use Vault to store some credentials for application also, but mostly for TLS certificates and credentials for different machines (Linux and Windows based). One of the best feature that Volt provides is the dynamic generated credentials a really powerful feature. Also it supports different platforms. Something where maybe a room of improvement is the interface, although it has a web UI, most of the configuration is done via CLI. Also a small minus will be the documentation that is available, because some times it isn’t give enough detail and sometimes can be frustrating configuring it. But, nonetheless this is a powerful and useful tool to have a layer of additional security.”
Conclusion
Choosing the encryption software that is right for you does not have to be difficult. Just take your time and go over the pros, cons, and pricing of all the ones you are interested in. The list above gives you a great place to start. You can’t go wrong using any of the encryption software programs on this list.The one you choose will be based a lot on personal opinion, as well as what may be right for your business based on what you need.





