10 Best API Security Tools
Security testing can be a time-consuming and expensive procedure. It is also a skill-intensive work. But how do businesses that can’t afford periodic security tests protect their data?
The solution is using an online vulnerability testing platform that automatically scans your API using several penetration testing procedures to identify open threats.
Top 10 Software
What is the Best API Security Tools ?
Here is a list of API security tools that do exactly that.
1. Wallarm
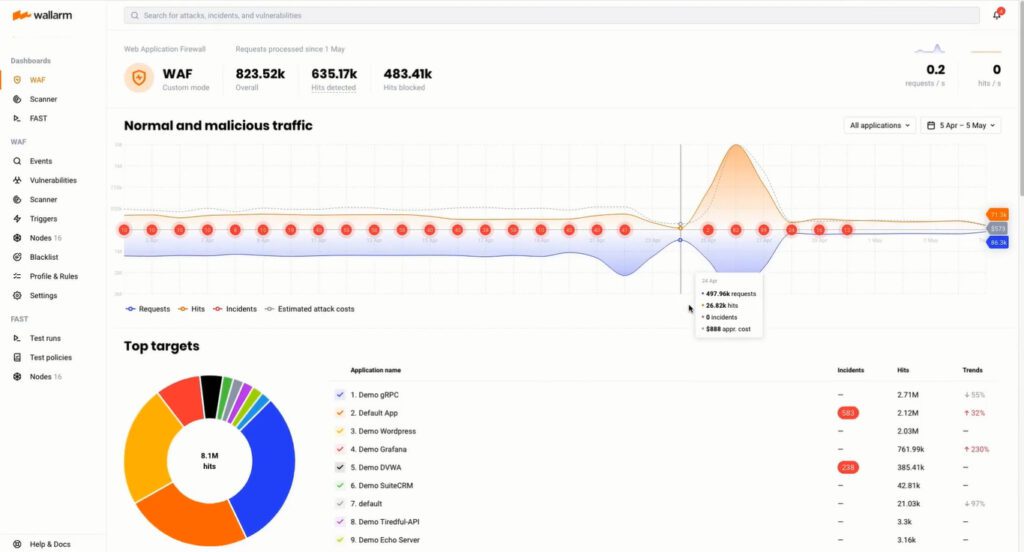
Wallarm one of the Best API Security Tools, it automates real-time application protection and security testing for APIs, apps, and microservices and APIs across multi-cloud and K8s environments. Wallarm is the only solution that unifies best-in-class API Security and WAAP (Next-Gen WAF) capabilities to protect your entire API and web application portfolio in multi-cloud and cloud-native environments. It can protect any API (REST, SOAP, graphQL, gRPC, Web Applications, Microservices, Serverless) in any environment:
- AWS, GCP, Azure, IBM Cloud
- Private, Hybrid and Multi-Cloud
- Kubernetes / Service Mesh
- Zero-Trust
Against any threats:
- OWASP Top-10 Threats
- API-specific Threats
- Credential Stuffing
- L7 DDoS and Bots
Security and DevOps teams choose Wallarm to discover all cloud-native APIs and legacy web applications running in their environment, and to detect & respond to threats against them in simple steps:
– Discover
Get the visibility, monitoring and protection capabilities across your entire API portfolio required to regain control over your API attack surface and reduce associated risk.
- Know your API Portfolio: Discover all your APIs, so you can improve control of your attack surface and reduce risk.
- Compare Actual to Spec: Automatically create OpenAPI (Swagger) specs based on actual traffic, so you can ensure security team has full visibility.
- Monitor Sensitive Data: Understand sensitive data usage, so you can ensure compliance and reduce risk of improper exposure.
- Segment your APIs: Differentiate assets in your portfolio, so you can tailor your security program to focus on critical needs.
- Monitor Changes in your APIs: Get alerts when new APIs pop up or when existing APIs change, so you can minimize API drift and guard against protection gaps.
- Detect & Respond to Threats: Quickly search for and assess latent or active threats, so you can remediate issues before they become problems.
– Protect
Go beyond OWASP Top 10. Get full coverage for API specific threats, account takeover, malicious bots, L7 DDoS, and more — in one platform.
- Best API Security: Protect your REST, SOAP, gRPC, graphQL, and WebSocket-based APIs.
- Single Dashboard: At-a-glance insights into security posture across your app portfolio.
- Tuning-free: No noisy alerts or false positives, or headaches to deal with.
– Respond
Streamline incident response with complete visibility, smart triggers, and active threat verification.
– Test
Automate security testing of your APIs and web assets. Prioritize remediation for every asset, in every environment.
2. Beagle Security
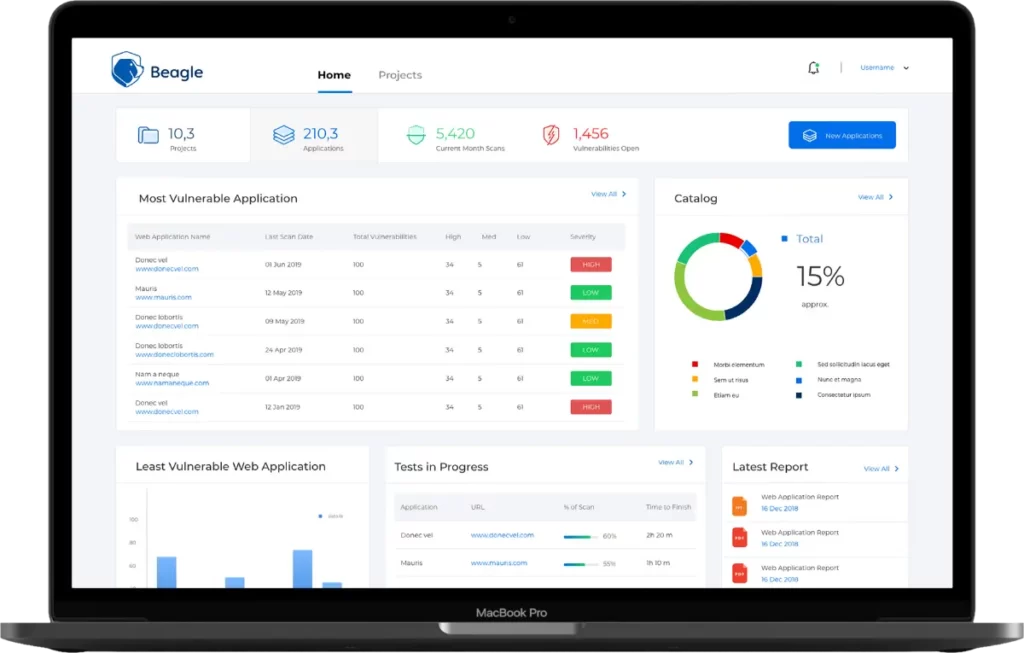
BeagleSecurity listed in the Best API Security Tools, is a web application penetration testing tool that helps you to identify vulnerabilities on your website & API security issues at the right time and address them in the right way before hackers exploit them.
Many new vulnerabilities get released regularly. You are leaving your business at serious risk if you don’t find them at the right time and fix the issues. With Beagle Security’s intelligent automation, you can schedule your website’s penetrating testing on a weekly basis to find any new security weaknesses and fix them immediately.
A development team’s primary focus is to write functional code. 83% of vulnerabilities occur due to mistakes that creep into the code without developers even realizing it. Integrating Beagle Security with the development pipeline will allow developers to identify vulnerabilities and make changes before an important update goes live.
It integrates with your development pipeline and communication apps, Beagle Security works with all major CI/CD pipeline tools and communication applications to make your work easier. You can also build your own integration with the API.
Beagle Security combines all the essential features at an affordable price so that your business and data is secure throughout:
- Intelligent Security: AI-powered core for test case selection & result verification.
- OWASP Top 10: Identify vulnerabilities documented by OWASP Top 10.
- SANS 25: Find SANS 25 vulnerabilities present on a website.
- Web & API Security: Discover security issues in your websites & APIs.
- Security Compliance: Stay compliant with global security standards.
- DevSecOps CI Plugins: Integrate security into the DevOps pipeline.
- Authenticated Testing: Security test complex web apps with login modules.
- Team Access: Invite teammates and collaborate easily.
- Schedule Tests: Easy scheduling of tests for continuous security checks.
- Integrations: Integrate with popular tools like Slack, Jira, Asana and Trello.
- Export Report: Export test results in multiple formats.
- Security Badge: Display a security badge and build trust with customers.
Beagle Security allows your team to focus on what really matters, building a great product for your customers and delighting them without compromising security by:
– Identify vulnerabilities:
Get to know all the security loopholes in your website from a hacker’s perspective.
– Website security score:
Understand the severity of each existing vulnerability and the overall security score of your website.
– Fix security issues:
Follow the steps in the penetration test reports to address security issues correctly.
3. StackHawk
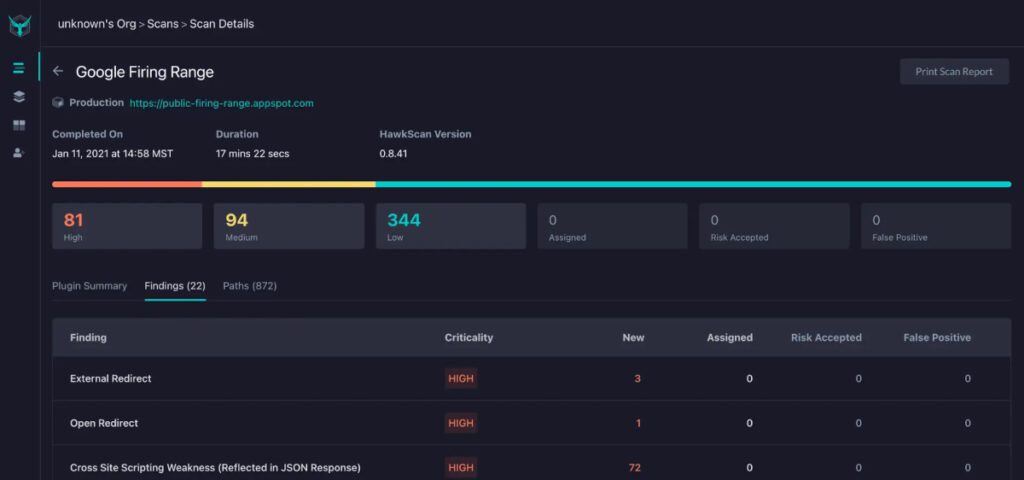
StackHawk tests your running applications, services, and APIs for security vulnerabilities that your team has to correct. With StackHawk, your application security tooling is just another part of your engineering stack. Integrating AppSec into your existing workflows is easy.
That’s how this platform works:
– On every new pull request, a StackHawk scan will run against your application, service, or API to find any newly introduced vulnerabilities from your code or your open source components.
– If alerted of a new security finding, developers have all of the information needed at their fingertips. With clear descriptions of the vulnerability and the request/response details that triggered the finding, developers can take action now or send to an existing team backlog.
– Developers can copy a cURL command to recreate the request that triggered the finding, leading them right to the bug. With links to fix documentation, remediating security bugs has never been faster.
As a dynamic testing tool, StackHawk is language agnostic and it tests:
- Server Side HTML.
- Single Page Applications.
- REST APIs.
- GraphQL APIs.
- Authenticated Applications.
With application security tests on every pull request, developers are alerted if they are about to introduce a new vulnerability into production. Equipped with all relevant information to troubleshoot the bug, including a cURL command to reproduce the finding, developers can quickly triage the issue, choosing to fix or prioritize in a future sprint.
Software is pushed to production faster than ever before, with many teams releasing multiple times per day. Legacy approaches to application security no longer cut it.
Weekly scheduled scans of the production application lead to delayed vulnerability discovery and vast inefficiencies in fixes. The future of application security is automated in CI/CD.
The requirements for AppSec testing are different now:
– Vulnerabilities Now Found Before Prod: Get alerted before a vulnerability is live in production, allowing you to control risk profile of what is shipped to customers.
– Fixes Are Faster While in Context: Developers are notified on the PR when a new vulnerability is introduced, allowing them to fix the code they just worked on.
– Change Increments are Smaller: Scanning underlying microservices and APIs creates faster scans and clearer focus when a fix is needed.
– Security Scales Across Engineering: With developer centric tooling, the age-old problem of security playing catch up with engineering is gone.
– Leverage Trusted OSS Scanner: Built on ZAP, StackHawk leverages the industry standard dynamic application security testing scanner.
– Test the Modern Application Stack: Engineering teams deliver APIs, GraphQL, and single page apps, so your AppSec tooling must be built to test the modern stack.
4. Salt
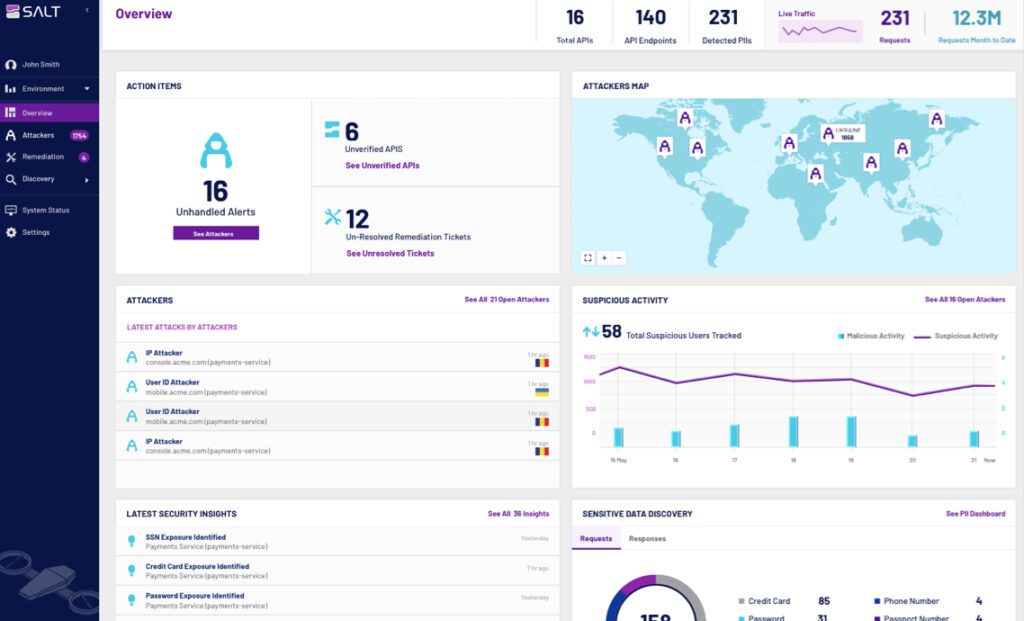
The Salt API Protection Platform discovers all APIs and their exposed data, stops attackers in their tracks, and provides remediation insights for developpers.
The Salt Security API Protection Platform secures the APIs at the heart of all your modern applications. The platform collects API traffic across your entire application landscape and makes use of AI/ML and a cloud-scale big data engine to discover all your APIs and their exposed data, stop attacks, and eliminate API vulnerabilities with scanning and testing in the build phase and remediation insights learned during runtime.
Salt is a complete API security for complete protection that enables you to:
– Discover all your APIs
Continuously inventory all your APIs, including shadow and zombie APIs.
– Prevent sensitive data exposure
Identify the APIs that are exposing PII or other sensitive data.
– Stop API attacks
Correlate activity to block attackers during reconnaissance.
– Prevent ATO, Data Exfiltration
Thwart credential stuffing, account takeover, and data theft attacks.
– “Shift left” with proactive API security
Test APIs in pre-production to identify and eliminate vulnerabilities.
– Accelerate incident response
Reduce the time needed to understand and resolve incidents.
– Provide remediation insights
Share learnings from runtime analysis with dev teams to harden APIs.
– Simplify compliance
Tie your API and sensitive data discovery and vulnerability remediation into GRC workflows.
Salt ensures a complete coverage, fueled by rich context in simple steps:
– Discovery: Only Salt provides intelligent aggregation and consolidation of your API inventory.
- Update inventory automatically and continuously
- Highlight “shadow” (unknown) and “zombie” (outdated) APIs
- Pinpoint APIs that expose sensitive data
– Runtime protection: Only Salt tracks users over days, weeks, and months to understand today’s drawn-out API attacks.
- Tap cloud-scale big data to baseline users and APIs over time
- Identify anomalies and distinguish mistakes from attacks
- Block attackers, not attacks – either manually or automatically
– Shift left practices: Only Salt leverages insights from bad actors’ minor successes in runtime to craft remediation insights.
- Analyze OAS/Swagger files for vulnerabilities
- Test APIs in pre-production, tuning attack simulations to the discovered APIs
- Pinpoint APIs that expose sensitive data
5. Reblaze
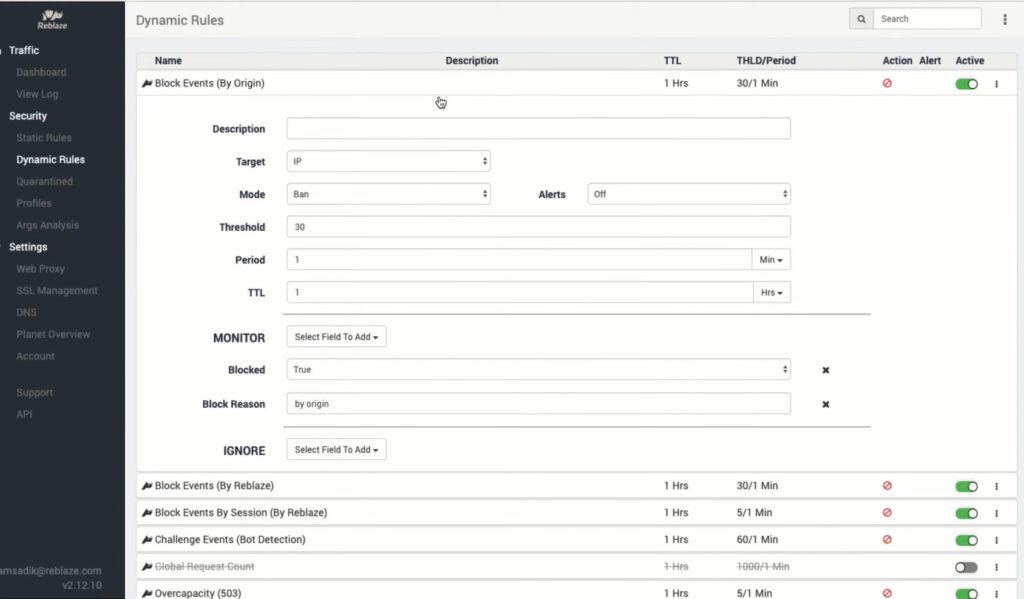
Reblaze provides proprietary security technologies in a single, unified platform, shielding your assets from the myriad of threats found on the Internet. Next-Generation protection for APIs: web services and microservices, mobile/native APIs and more, on the clouds, making your web assets secure by default. Reblaze is deployed as a reverse proxy in a Virtual Private Cloud, geolocated immediately in front of the protected network. Incoming traffic is routed through the VPC and scrubbed as it passes through.
Reblaze provides complete protection for microservice/API endpoints:
– A client-side SDK ensures mobile/native application traffic is TLS encrypted and continuously authenticated. All communications include an HMAC signature (a cryptographic identity mechanism on the client side) to harden communications between the application and the endpoint, ensuring that only requests from legitimate users are accepted
– API schema ingestion, validation, and enforcement provides automated protection
– Reverse-engineering prevention stops API attacks in their earliest stages
– Dynamic and adaptive traffic recognition allows Reblaze to reshape its security posture in response to changes in traffic structure. As an API evolves, Reblaze creates new rulesets automatically, and administrators can accept, reject, or modify them as needed
– Cloud-native platform includes a full API for programmatic control of Reblaze itself, enabling IaC and other forms of automation.
Along with API security, Reblaze provides complete protection for sites and web applications as part of its all-in-one solution:
– Next-generation WAF blocks malicious traffic.
– All-layer DDoS protection for both web traffic and API endpoints, auto scaling cloud resources to absorb and defeat even massive volumetric assaults.
– Advanced bot detection: Modern attack bots have become quite sophisticated and difficult to identify. Reblaze is a pioneer in advanced human/bot detection technologies, defeating even the latest generation of malicious bots which can mimic human behavior.
– Fully managed: Your Reblaze platform is kept up-to-date by a team of security experts. You always have the latest protection, with no effort required from your IT staff.
– Dedicated Virtual Private Clouds for every account. This eliminates the multi-tenancy vulnerabilities that other solutions have, while reducing latency to negligible levels (typically three milliseconds or less).
– Runs natively on the top-tier cloud platforms, with your choice of configuration. Reblaze can also be used in hybrid mode.
– Self-learning platform uses Machine Learning to recognize, and adapt to, changing Internet traffic conditions. Even as new web threats arise, your sites, applications, and endpoints remain secure.
Reblaze’s API defenses extend far beyond common threats such as DDoS and code injection. The platform recognizes and defeats even subtle application-layer attacks, such as data scraping, gift-card and coupon abuse, inventory denial attacks, and more.
6. Apigee
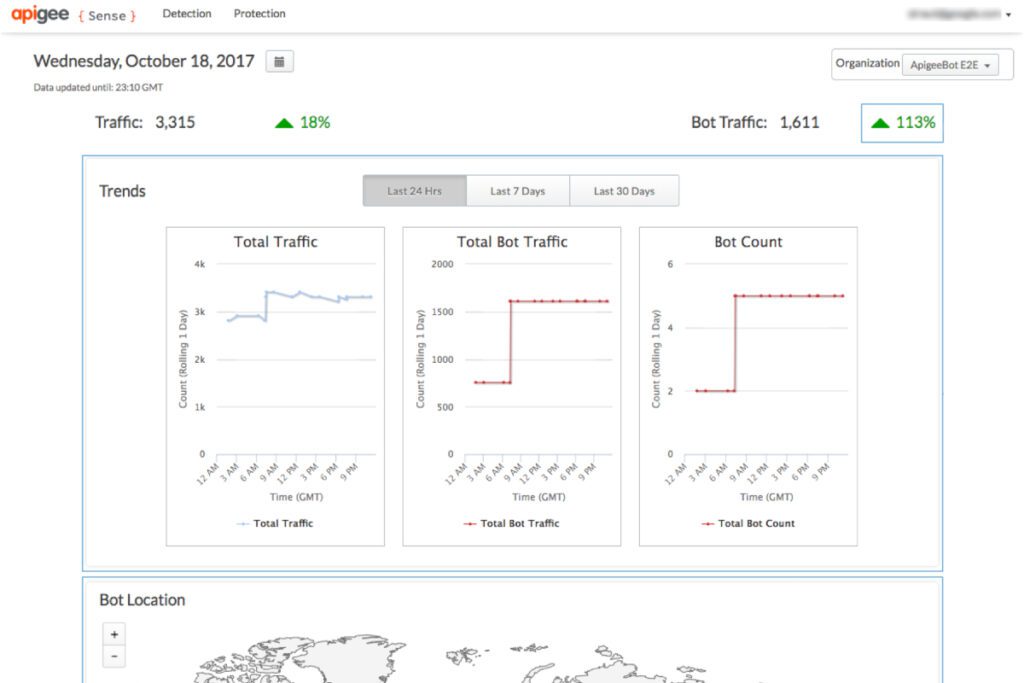
Apigee Advanced API Security protects your APIs from attacks by malicious agents, such as bots. Apigee provides two main tools for identifying threats and vulnerabilities: Bot detection. Identifying API misconfigurations.
API security involves controlling access to your APIs, guarding against malicious message content, accessing and masking sensitive encrypted data at runtime. Apigee protects APIs against bot attacks, identifies and alerts administrators to suspicious API behaviors and automates protection against future attacks.
With Apigee Sense, you can protect your APIs from request patterns that include:
– Automated behavior that blends with human behavior.
– Persistent attempts from the same IP.
– Unusual error rates.
– Suspicious client requests.
– Data crawling.
– Key harvesting.
– Activity bursts.
– Geographical patterns.
Behind the scenes, Apigee Sense does its detecting from your request metadata, then provides its analysis results for you to review. You can review the analysis results in the Apigee Sense console. When a pattern looks suspicious, you can take a closer look at details behind it to decide whether to take action.
To detect request patterns, Apigee Sense stores and analyzes request metadata. As clients make requests, Apigee Sense collects request metadata, then analyzes that data in batches to look for patterns.
The benefits of this platform are:
– Intelligent API security: Analyze call patterns from API metadata captured on the and use algorithms that identify anomalies autonomously.
– Behavior detection: The analysis engine examines metadata and characterizes every client request, flagging those whose patterns look suspicious—including detecting API-layer threat patterns and monitoring background behavior.
– API protection: Get alerts when a suspicious client is identified, so administrators can determine policy implementation. Apigee Sense automates responses to threats based on administrator rules, running in the background.
Key features of Apigee are, in the purpose of protecting your APIs from attack:
– Advanced risk analytics:
Visual dashboards that provide bot analytics, trends, and actionable intelligence.
– Automated risk mitigation:
Configurable countermeasures like blocking, throttling, and ensnaring of bots.
– Complete API security solution:
Complete one-stop API security infrastructure to protect API traffic.
– Data-driven risk models:
Monitor billions of API calls, identify anomalies, and uncover bad bot patterns.
7. Nevatech

Nevatech Sentinet is a powerful, flexible, lightweight and scalable API Management and API Governance software platform that will comprehensively address all your API Management needs. Sentinet software solution addresses the common challenges by taking full responsibility to provide cost-effective management and control for your APIs, and helps developers and operations to focus on the essence of the APIs’ business execution.
Think of any API Management feature or deployment model and you will find it covered by Sentinet with unprecedented ease of use and completeness of capabilities. The features explained:
– API Security:
Along with the ease of API integrations come the difficulties of ensuring proper API security. Sentinet API Management provides with flexible and comprehensive protection of APIs with API security, as well as implementations of API security when API Gateways make calls to your backend or partner APIs. Sentinet ensures your APIs comply with your strategy for data Privacy, Non-Repudiation and Attack Prevention.
– API Monitoring:
- Monitor usage and performance of your REST APIs and SOAP services in real-time. Build historical and analytical reports.
- Configure monitoring metrics and their thresholds with Service Level Agreements and violation Alerts. Predict future API usage and performance degradations before they happen.
- Search and filter message exchanges by date/time, status, communication and API errors, by API consumer, API operation and by messages content.
- Control how much and what information will be recorded about API calls.
– API Analytics:
Sentinet provides automatic and continuous data collection and data aggregation for extensive reporting and comprehensive analytics. Anticipate future usage, performance and scalability needs with Sentinet predictive analysis.
– Messages Transformation:
Sentinet provides configurable and automated conversions from different communication and message exchange protocols. For example, HTTP to non-HTTP or SOAP to REST.
– API Routing:
Route messages to different APIs or different versions of the same API.
Use Sentinet to load-balance API calls between API physical locations.
Reroute messages to alternative API locations from failed locations.
Graphically configure routing options.
– API Discovery and Description
Discover SOAP services and REST APIs from the Sentinet API Catalog.
Provide developers and your partners with the access to your services and APIs metadata, documentation and code samples.
– Dependency Tracking
– Version Control
– SLA Management
– Alerting
– Audit and Change Notifications
– Testing
8. Cequence
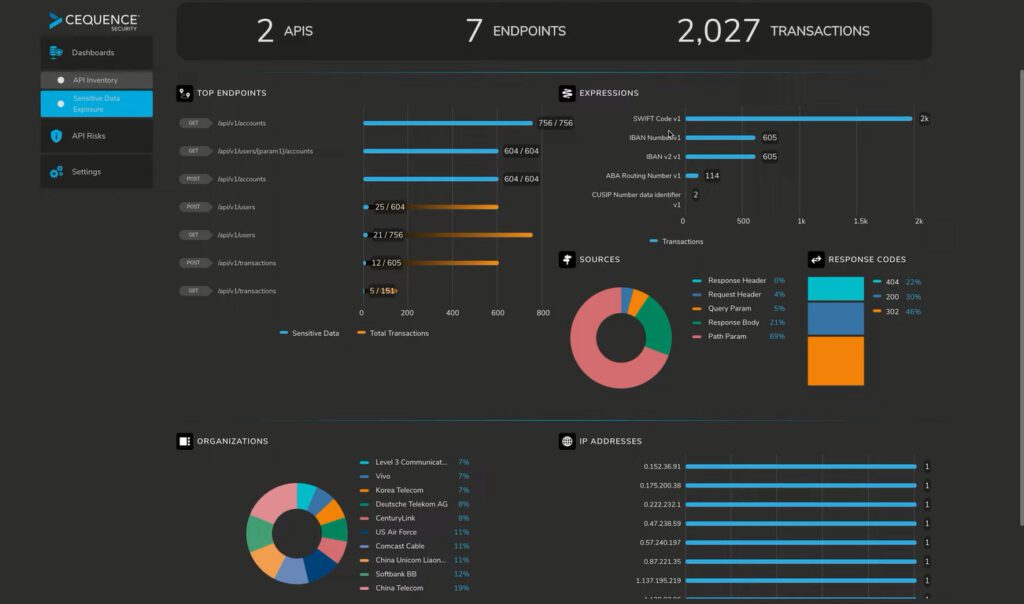
Cequence Unified API Protection solution. Eliminate unknown, unprotected and unmitigated API risks. The Cequence UAP creates a complete runtime inventory of all managed and unmanaged APIs, known and previously unknown. Discovered APIs risks are flagged for remediation while sophisticated threats are detected and mitigated in real time. The result is complete protection from API threats that cause data loss, theft, fraud, and business disruption.
An End-to-End API Protection solution, that let you:
– Discover:
Discover what your attackers see without any agents or software to deploy, and prioritize issues by severity of discovered risks.
– Inventory:
Create a real-time inventory of your managed and unmanaged APIs. Uncover and remediate those that may be exposing sensitive data, not following specification definitions, or failing to use authentication best practices.
– Compliance:
Ensure adherence to security and governance best practices and standards by providing compliance assessment and remediation.
– Detect:
Hundreds of predefined behavioral fingerprints, rules, and machine learning models (leveraging the largest threat intelligence database on the market) provide high-efficacy detection of automated attacks and exploits such as those defined by OWASP.
– Prevent:
Native, real-time attack responses eliminate the need to signal external security devices such as a WAF. Choose from multiple response options configurable on a per-policy or per-API or app basis.
– Test:
Leverage the most up to date attack surface views, plus uses predefined API-specific tests based on OWASP threat definitions and advanced techniques to find and fix vulnerabilities during pre-production.
Deploy the Unified API Protection solution with zero changes to your on-premises, cloud or SaaS infrastructure, or modifications to your existing API or web application workflows. Quickly expand coverage, visibility, and mitigation across the entire API protection lifecycle—without disrupting or slowing business.
Cequence is different because of: One-Click deployment, unmatched threat intelligence, broadest set of network integrations and the maintain data privacy.
9. Edgescan
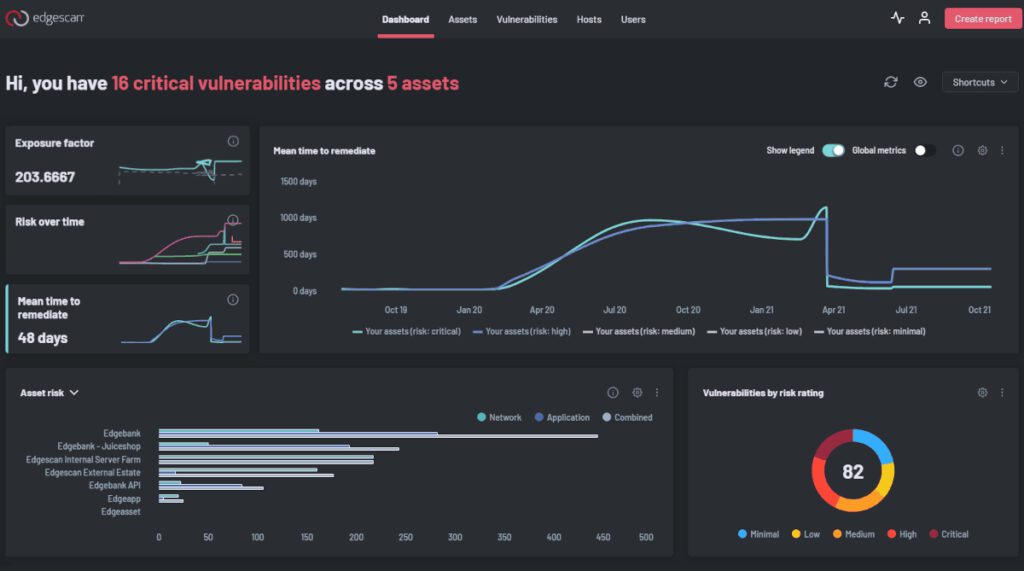
Edgescan Smart Vulnerability Management is an award-winning & internationally accredited cyber attack prevention and continuous security testing.
The Edgescan platform provides a multi-faceted approach to providing coverage to the full development stack, scaling up or down with the demands of your attack surface. Your attack surface is continually monitored to discover vulnerabilities such as rogue APIs or legacy/shadow assets.
PTaaS combines human expertise on top of Edgescan technology and commonly used consultant tools, such as automated static and automated dynamic analysis, when assessing high assurance applications. Automated scans are set up for all known CVEs and OWASP vulnerabilities and run against all entities in your attack surface.
Edgescan is constantly improving and adding to the platform to provide continuous, feature-rich attack surface monitoring and live vulnerability tracking. In addition to the already existing features:
– Threat Intelligence & Risk-based Prioritization
The new threat intelligence & risk-based prioritization feature enables a new view for Enterprises to cross-reference their vulnerabilities with the CISA exploit list.
– Centralized Dashboard
Get all your information in one location with an interactive & exportable risk metrics dashboard.
– Assets
Keep track of all assets and perform assessments on demand for a holistic management of your organization’s assets.
– Vulnerabilities
Receive actionable risk intelligence with the ability to rescan on demand to ensure that your hosts, assets, and vulnerabilities are fixed. Vulnerabilities will tell you the following information at a glance: ID, name, location.
– Hosts
Always know what’s going on with 24/7/365 visibility of your external exposures that have been added to the platform.
– Reporting
The Edgescan platform has an extensive reporting system that allows you to generate a report on any page that you are on, via standard reporting or PCI reporting.
– Events & Integrations
Create live alerts for any changes and connect the platform into many other services, allowing you to extend the capabilities of your security team.
– Rapid Support
Edgescan has a full-time rapid support team to offer assistance and a virtual pen testing team available on demand.
10. Moesif
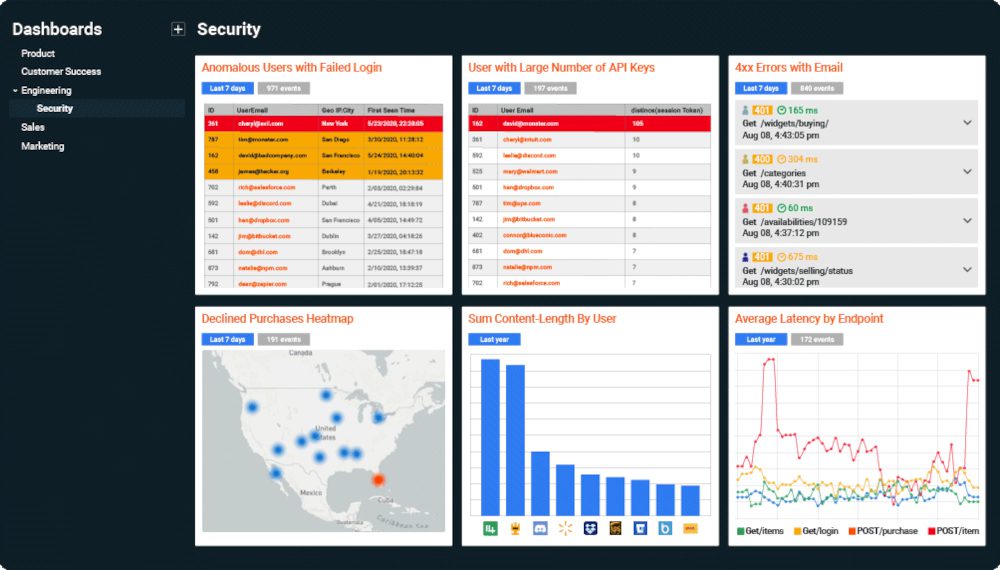
Moesif detects and protects against API security threats with user behavior analytics (UBA) and governance using plugins for NGINX, Kong, and more. Your API is the gateway to your data, yet customer API traffic and bot traffic look the same which means outdated rules from traditional web application firewalls (WAF) and browser fingerprinting won’t work. Leverage advanced user behavior analytics (UBA) to detect and protect against API security threats before data is leaked.
Reduce not only your own security risk, but also reduce your customers’ risk. Automatically notify them when they’re using an insecure implementation or let them know when they are rate limited.
Moesif has implemented robust security procedures throughout the platform and organization. Moesif maintains an active SOC 2 Type 2 attestation available on request and is a big believer in zero-knowledge and multi-layer security for protection of your data. The founding team are engineers that have worked on applying microcode patches securely at Intel to processing and storing sensitive payment data at Microsoft.
What you will have with Moesif:
– Detect security vulnerabilities
Understand API usage by countries, user agents, API keys, and more.
Detect suspicious API behavioral flows that don’t match typical users.
Lower privacy and compliance risk with audit logs of all API accesses with long data retention policies.
– Identify suspicious users
Identify suspicious user behaviors and prevent repeat offenders.
Get alerted when users use your APIs inappropriately or scrape large amount of data.
Automatically warn customers using a vulnerable or insecure implementation.
– Block API abuse and threats
Block users automatically based on bad behavior and unusual access patterns.
Leverage advanced anomaly detection to stop zero-day exploits that rule-based scans miss.
Get started in minutes with developer-friendly SDKs and plugins for most API gateways and languages.
It integrates with your analytics stack:
– Analytics
Track customer usage across web and API products to drive personalized campaigns.
– Billing
Monetize your APIs effortlessly with robust and easy-to-make usage-based meters.
– CRM
View trial usage in your CRM and automate outreach for expansion and retention goals.
– Alerting
Get alerted on performance issues, security threats, and more.
Conclusion
With the API security ranking as a top priority in 2022 for enterprises and security leaders worldwide, and the market being crowded with vendors. Our list of ten API security solutions that ensure API protection is meant to select the best, one of them can be the right fit for your organization.





