10 Best Malware Analysis tools
In simple words, malware or malicious software, is any program or file that intentionally damages a computer, network, or server.
To prevent that from happening malware testing tools scan an executable’s code for specific actions in memory that show typical activity or contact a command and control server and identify the system as malicious.
Top 10 Software
What is the Best Malware Analysis tools ?
1. INTEZER
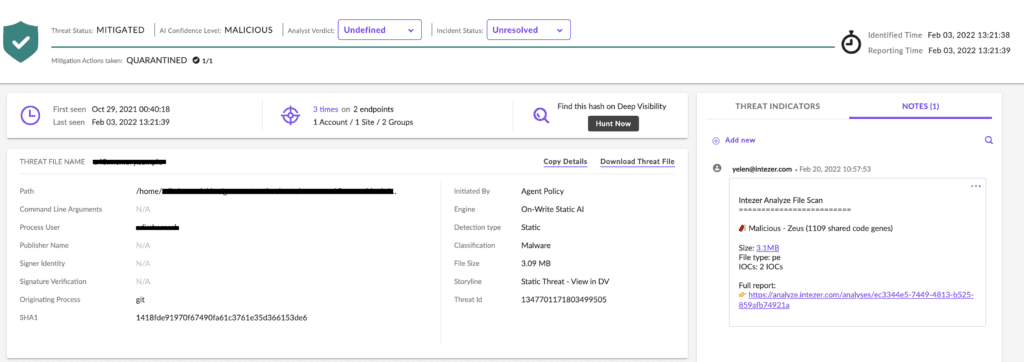
INTEZER, one of the Best Malware Analysis tools is a malware analysis tool that generates automated alert triage, enabling 24/7 monitoring and in-depth investigation of endpoint and email alerts. It also helps you reverse engineer any suspicious files and processes, identifies and automatically remediates false positives, and contextualizes alerts based on suggested actions and risk profiles.
With Automated Response, you get actionable IOCs with clear instructions for easy remediation, full in-memory analysis of DFIR and suspicious endpoints, behavioral rules for finding and remediating additional infections, and proactive escalation for critical incidents.
Use automatic huntFind stealthy attacks that go undetected by existing tools, continuously scan your environment for APT and cybercriminal activity, track threat actors and families for ongoing detection opportunities, and access extensive search rules.
The software provides out-of-the-box integrations for EDR, SOAR, SIEM, and more. Eliminates most false positives and reduces alert response time by 90%.
Besides, you can automate phishing investigations, using Intezer to triage suspicious links and email attachments.
2. VIRUSTOTAL
Virustotal is a free service that analyzes files and URLs for viruses, worms, Trojans, and other types of malicious content. Their goal is to make the Internet safer through collaboration between antivirus industry members, researchers, and end users of all kinds.
VirusTotal checks articles with 70+ antivirus scanners and URL/domain blacklisting services, in addition to using various tools to extract signals from checked content it also offers several file transfer methods, including the main public web interface, desktop uploaders, browser extensions, and programming APIs.
This core analysis is also the basis for several other features, including the VirusTotal community: a network that allows users to comment on files and URLs and share notes.
VirusTotal can be used to detect malicious content as well as to identify false positives — items that have been identified as malicious by one or more scanners, which are benign and harmless.
Malware signatures are frequently updated by VirusTotal because they are distributed by antivirus companies. This ensures that our services use the latest set of signatures. Additionally, it is free for end users for non-commercial use.
3. ANYRUN
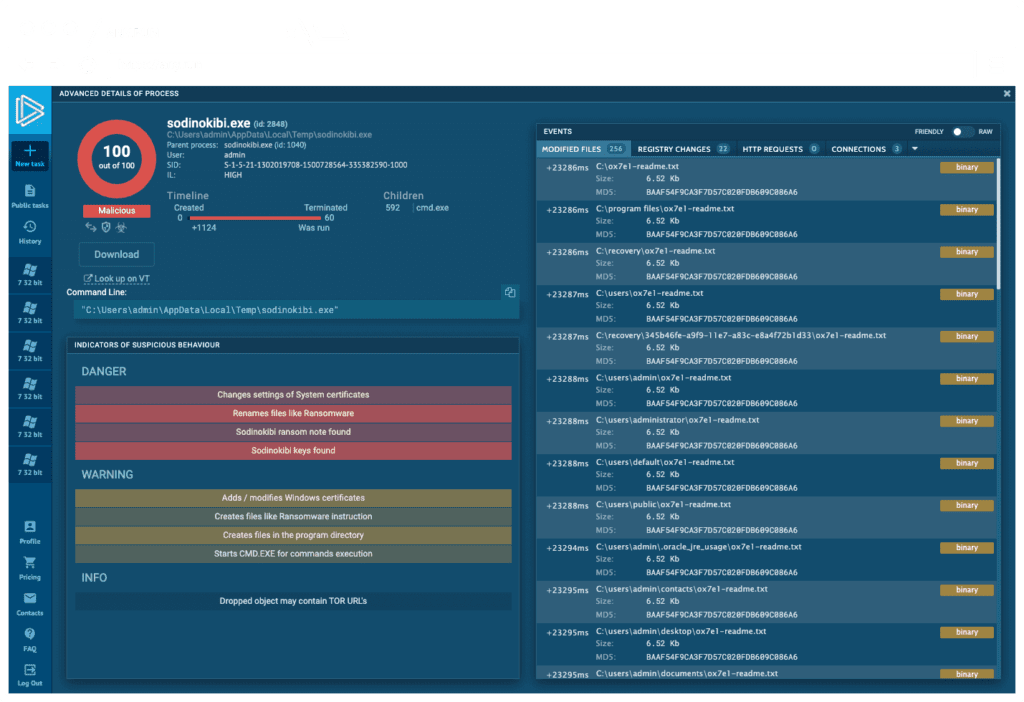
AnyRun is an innovative cloud-based sandbox with fully interactive access. The service shows many aspects of testing such as: Creation of new processes, potentially suspicious or malicious files or URLs, as well as registry activity, network requests, etc. in real-time to make conclusions during task execution without waiting for final reports.Your threat intelligence platform allows you to collect and analyze attacks as they occur and detect IOCs early on. Malware reports are available through public submissions and downloaded in a special format.
The information security audit tool provided by the service allows to generate reports containing important malware analysis such as videos, screenshots, hashes and any data collected during the execution of the task. The service also provides the ability to collaborate in single desktop mode or host live presentations for multiple people.
The interactive nature of their services makes it possible to obtain the first results immediately after starting a task, without having to wait for the simulation to be completely over.
The software also offers interactive analysis, simplification of the analysis algorithm, fast generation of results due to the interactivity of the process, UX – intuitive user interface, reduced equipment cost and a large malicious database that allows you to get the latest data, hashes and IOCs virtually It’s an instant.
4. CORO
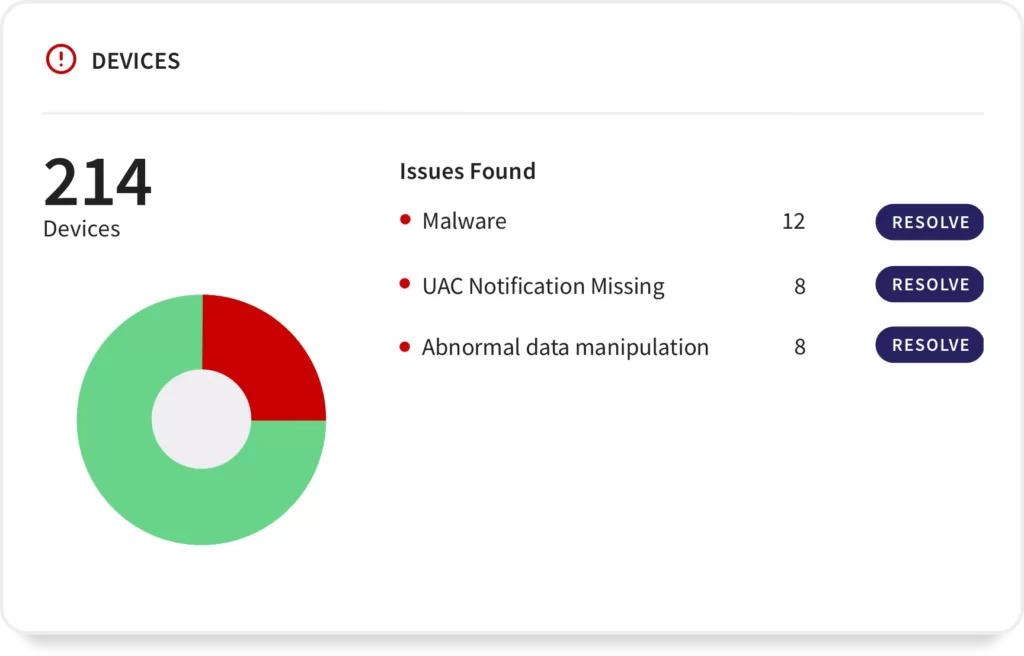
Coro is an All-in-one network protection that is easy to install and operate, and allows IT to quickly configure what is and is not critical to your organization’s security.
Coro removes the complexity of network security, enabling your administrators to manage your organization’s security without disrupting business operations, user productivity, or wasting valuable IT time.It is a central control point for sensitive data, practice data and user activity, enabling you to enforce a wide range of security, compliance and governance policies.
The software scans every email for phishing, malware, ransomware or any PII/PCI/PHI data sharing to prevent confidential information leaks, automatically remediate threats, automatically identify insider threats, account hacking and malicious activity and to block.It integrates with Salesforce, Dropbox, Box and more.
Coro’s key features are :
- Protects your entire business: users, cloud apps, email, devices, data.
- Covers all threats: malware & ransomware, phishing, hacking & access control, insider threats and data governance.
- Threats detection free forever.
- Free remediation for 14 days.
5. WILDFIRE

WILDFIRE cloud-based threat analysis service is the industry’s most advanced analysis and prevention engine for highly evasive zero-day attacks and malware.
It combines machine learning, dynamic and static analysis, and a custom analysis environment to uncover the most sophisticated threats across multiple stages and attack vectors.
With this tool you can:
- Keep your files safe with the industry’s largest threat detection and malware protection engine that automatically detects and protects against unknown malware up to 180x faster.
- Analyze twice as many unique malware samples per month than security teams’ preferred sandboxing engine, while inline ML instantly blocks fast-moving malware like ransomware and fast-moving threats on the firewall.
- Accelerate your security with faster updates up to 180x faster than any other sandboxing solution.
- Automated cloud-to-crowd protection with cloud-based architecture for any network, endpoint,and cloud locations from malware seen once in the largest cybersecurity customer network.
- Complete coverage to secure your organization globally, WildFire can be consumed as a public service as well as deployed in hybrid and air-gapped environments.
6. FILESCAN.IO

FileScan.IO is a free malware analysis tool that offers fast file assessments, threat intelligence and indicator of compromise (IOCs) extraction for a wide range of executable files, documents and scripts.
The main focus of FileScan.IO is not only to detect malicious files, but also to extract potential “Indicators of Compromise” (IOCs) from compressed, obfuscated and encrypted data. This process is performed using a proprietary simulation engine on a large scale and at high speed compared to traditional dynamic analysis.
This includes recursive analysis of all download URLs, base files, and all extracted artifacts. Additionally, all files are scanned for hundreds of malicious threats and policies, and where possible mapped to the MITER ATT&CK framework for faster assessment.
FileScan.IO’ main benefits :
- Perform detection and IOC extraction for all common threats (files and URLs) on a single platform.
- Quickly identify threats and their capabilities, and update your security systems.
- Scan your corporate network for infected endpoints.
- API-driven framework for easy integration into existing systems.
- Simple reports for entry-level analysts and executive summaries and more.
7. FileWall for Microsoft 365
FileWall for Microsoft 365 is one the malware analysis tools for windows that offers ultimate protection against file-based cyber-attacks for Microsoft 365 business applications.Utilizing odix’s patented Deep File Analysis (DFA) technology and proprietary Content Disassembly and Reconstruction (TrueCDR™) algorithm, FileWall ensures efficient removal of embedded malicious code in commonly used files.
The DFA process treats files as the tip of an iceberg, often invisible on the surface, but digs beneath the surface and eliminates embedded malware in files that traditional legacy solutions go undetected. FileWall complements Microsoft’s security products such as Exchange Online Protection (EOP) and Microsoft Defender (formerly known as Advanced Threat Protection – ATP).
Reasons why you should try this software:
- Valid for external and internal users.
- Protect against known and unknown attacks.
- Close the security grap for Microsoft EOP and defender.
- High level of client adoption with no sandbox-related delays.
- Deep files analysis inc. Nested file, archives, password-protected ect.
8. CUCKOO SANDBOX

Cuckoo sandbox is the leading open source automated malware analysis system that automates the task of analyzing malicious files on Windows, macOS, Linux and Android. Thanks to Cuckoo’s open-source nature and extensive modular design, every aspect of the analysis environment, analysis results processing and reporting phases can be customized.
Cuckoo gives you everything you need to easily integrate your sandbox into existing frameworks and backends, the way you want, in the format you want, and all without licensing requirements.
it can:
- Analyze many different malicious files (executables, Office documents, PDF files, emails, etc.).
- Track the general behavior of API calls and files and distill them into common messages and signatures that everyone can understand.
- Secure and analyze web traffic even if it is encrypted using SSL/TLS.
- Use YARA to perform advanced memory analysis of compromised virtualized systems with volatility and process memory granularity.
9. HYBRID ANALYSIS
Hybrid analysis provides a free community malware analysis service that detects and analyzes unknown threats using a unique hybrid analysis technique.The tool covers the entire attack lifecycle, with detailed insights into all file, network, storage and process activity. With easy-to-understand reports, actionable IOCs, and seamless integration, you can save time and increase the efficiency of all your security teams.
Analytics reports provide new levels of visibility into real-world threats, enabling teams to make faster, better decisions and improving the capabilities of all members.
Use hybrid analysis to:
- Gain insight into who might be targeting you and how to protect yourself from them.
- Instantly see if malware is related to a larger campaign, malware family, or threat actor, and automatically expand analysis to include all related malware.
- Choose full control (including custom images) and use the local option to deploy specifically to your environment.
- Easily integrate into SIEMs, TIPs and orchestration systems with an easy-to-use REST API, pre-built integrations, and support for indicator sharing formats including STIX, OpenIOC, MAEC, MISP, and XML/JSON.
10. PT MultiScanner
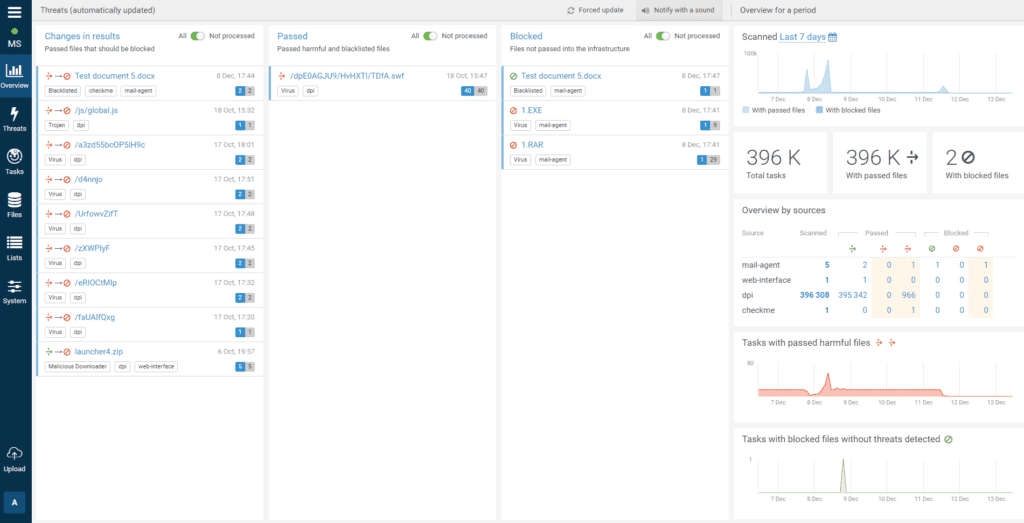
PT MultiScanner is a malware solution that provides multiple levels of anti-malware protection to detect and block infections on corporate infrastructure, uncover hidden threats, and simplify investigation of malware-related security incidents.This solution supports scanning of files and archives, including recursively compressed ones.
The main features are :
Multi-Vendor Approach to Maximum Malware Detection: PT MultiScanner detects and blocks malware more effectively than any siled approach.
Discover new and hidden threats with retrospective analysis: it detects stealthy malware buried deep in your infrastructure as well as the latest threats.
Comprehensive coverage of all data: the solution detects and blocks malicious activity across the entire corporate infrastructure: web traffic, web traffic, file storage, web portals, and email (attachments to the most popular file extensions such as .docx, .xlsx cleanup) ., .rtf, .pptx, .pdf, .html, .jpg, and .zip).
Quick Locating: PT MultiScanner locates all stages of malware propagation and affected users, enabling successful incident response and efficient investigation.
Simple and fast deployment: Add the software quickly and easily to existing infrastructure through standard interfaces: SPAN, MTA, ICAP or REST API.
Scalability and high availability: it’s a perfect fit for cluster deployment in active–active configuration with one central management console.
Conclusion
At the end of the article Best Malware Analysis tools, To sum up, not all malware analysis tools are created equal. Some tools require a higher level of skill, while others provide advanced analysis automatically. So be wise when choosing the right one for your.





