10 Best Managed Detection and Response (MDR)
Serious incidents emerge in organizations, when those lack the time or expertise to properly remediate the situation. Managed detection and response (MDR) has emerged as an answer to this market need. MDR helps an organization by implementing or improving threat detection, response, management and continuous monitoring capabilities all delivered as a service.
Top 10 Software
What is the Best Managed Detection and Response (MDR) ?
The main benefit of MDR is that it helps rapidly identify and limit the impact of threats without the need for additional staffing. This post has been created to walk you through the best managed detection and response services in the market.
1. Sophos
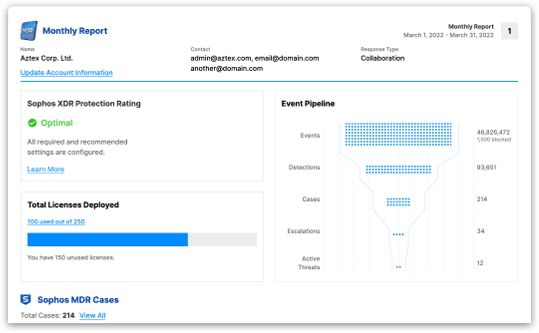
Sophos MDR security delivered as a service is a fully managed service delivered by experts who detect and respond to cyberattacks targeting your computers, servers, networks, cloud workloads, email accounts, and more. It detects more cyberthreats than security products can identify on their own, the experts detect and neutralize threats faster than other vendors.
This advanced MDR (Managed Detection & Response) security services fuse machine learning technology and expert analysis for improved threat hunting and detection, deeper investigation of alerts, and targeted actions to eliminate more sophisticated and complex threats.
What it does is:
– High-Fidelity Detection: Going beyond traditional threat detection, combining deterministic and machine learning models to spot suspicious behaviors and the tactics, techniques, and procedures used by the most advanced adversaries.
– Proactive Defense: Intercept X proactively protects customer environments by combining threat intelligence with newly-discovered Indicators of Compromise (IoC) and Indicators of Attack (IoA) that are identified through analyst-led threat hunts.
– Elite Expertise: A highly-trained team of threat hunters, engineers, ethical hackers, and SOC specialists has your back 24/7, investigating anomalous behavior and responding to threats with speed and precision.
– Outcome-Focused Security: Every threat hunt, investigation, and response results in actionable, decision-driving data that is then used in automation to enhance configurations and detection capabilities.
– Complete Control: You own the decisions. Control how and when potential incidents are escalated, what response actions (if any) you want us to take, and who should be included in communications.
Sophos MDR has advanced services, it includes all standard features, plus the following:
- 24/7 Leadless Threat Hunting: Applying data science, threat intelligence, and the intuition of veteran threat hunters, combine your company profile, high-value assets, and high-risk users to anticipate attacker behavior and identify new Indicators of Attack (IoA).
- Dedicated Threat Response Lead: When an incident is confirmed, a dedicated threat response lead is provided to directly collaborate with your on-premises resources (internal team or external partner) until the active threat is neutralized.
- Direct Call-In Support: Your team has direct call-in access to the security operations center (SOC). An MDR Operations Team is available around the clock and backed by security support teams spanning 26 locations worldwide.
- Enhanced Telemetry: Threat investigations are supplemented with telemetry from other Sophos Central products, extending beyond the endpoint to leverage automation and provide a full picture of adversary activities.
- Proactive Posture Improvement: Proactively improve your security posture and harden your defenses with prescriptive guidance for addressing configuration and architecture weaknesses that diminish your overall security capabilities.
- Asset Discovery: For both managed and unmanaged assets like IOT devices , provide valuable insights during impact assessments, threat hunts, as well as part of proactive posture improvement recommendations.
2. ArcticWolf
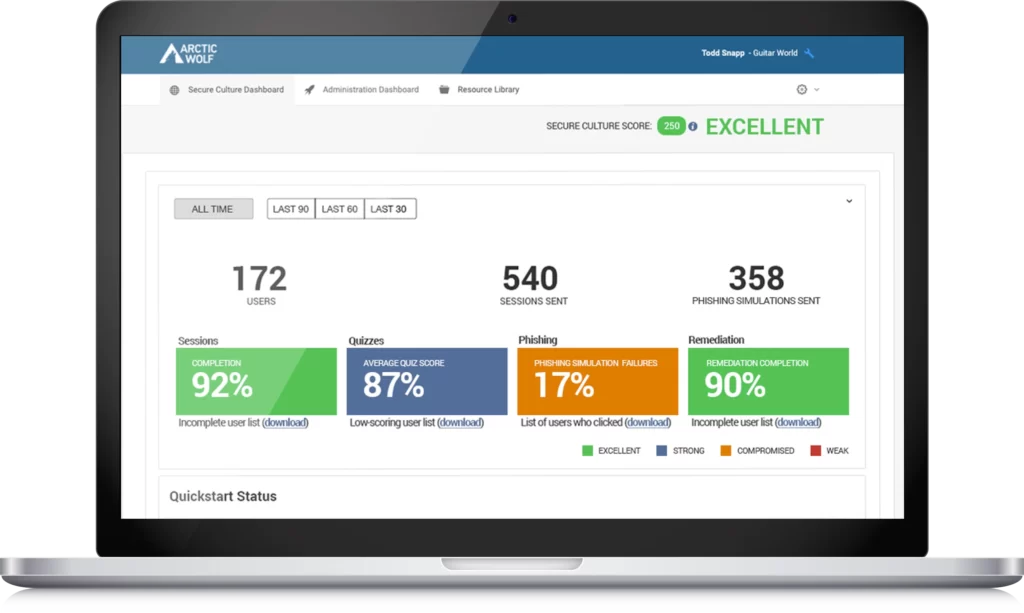
ArcticWolf MDR solution provides 24×7 monitoring of your networks, endpoints, and cloud environments to help you detect, provides a holistic, integrated and agile approach to improving your security posture. By providing round-the-clock monitoring, protecting your organization in real time and taking that data to routinely enhance security posture. Security experts execute alert triage and response, saving your organization time and money.
Hunt down cyberattacks before they impact your business by:
– Network Inspection: Continuous network traffic inspection that detects malicious activity to/from suspicious IP addresses and domains.
– Log Analysis & Search: Automatically collects, normalizes, analyzes and retains log data from existing networks, systems, and applications.
– Threat Detection: Identifies malicious files/EXEs, malicious traffic, bad IP addresses/domains, and lateral movement through Windows event log and Sysmon monitoring.
– Cloud Security: Monitors cloud services, SaaS apps, IaaS infrastructure, and SecOps services to identify malicious user activity.
– 24×7 Monitoring: A cloud-based SOC staffed by security analysts who monitor your on-premises and cloud resources 24×7.
– Managed Containment: Detect indicators of compromise and prevent the spread of threats.
– Endpoint Visibility: A unified endpoint technology provides operational metrics, asset categorization, threat visibility, and detection and response.
– Incident Response: Identifies critical security incidents from millions of suspicious investigations, escalates responses, and proposes remediation action.
At the core of the progressive SOC-as-a-service sits the industry’s original Concierge Security Team-security engineers working as an extension of your threat intelligence team around the clock. Keeping your business safe and secure in an ever-changing environment, they’re experts who know how to stay ahead of threats to:
– Prevent Intrusion:
Quickly identify vulnerabilities in existing systems
Continuously scan systems, advanced intelligence gathering, and proactively hunt threats
Prioritize remediation based on potential business impacts
Obtain a complete picture of assets, threat assessment, and on-demand remediation guidance
– Detect and Monitor Cyberthreats
Around the clock eyes-on-glass monitoring of network traffic
Unlimited ingestion of logs and lightweight agent
Continuous Cloud monitoring and improved threat detection
Dedicated Concierge Security Teams Provide 24×7 Incident Support
– Contain and Respond to Incidents
Dynamic Custom rule engine provides real-time issue escalation
Containment capabilities to quarantine incidents before they impact your networks
Seamlessly extend your SecOps team with named Concierge Security Team + Hybrid AI.
3. Huntress
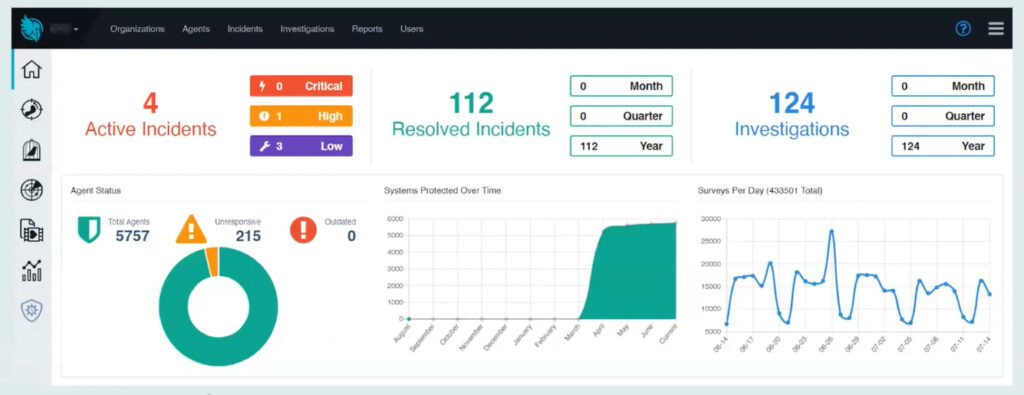
Huntress one of the best Best Managed Detection and Response (MDR) Software delivers a powerful suite of managed endpoint detection and response (EDR) capabilities, backed by a team of 24/7 threat hunters, to protect your business from today’s determined cybercriminals.
Deploy your safety net as Huntress protects your business throughout the modern attack lifecycle, defending against threats like ransomware, malicious footholds, and more. Add ThreatOps to your arsenal with security experts that take care of the heavy lifting with 24/7 threat hunting, world-class support and step-by-step instructions to stop advanced attacks.
Cut through the noise, it reviews all suspicious activity and only send an alert when a threat is verified or action is required, eliminating the clutter and false positives found in other platforms. Empower your staff aith one-click remediation, handwritten incident reports and powerful integrations, even non-security staff can use Huntress to swiftly respond to cyber events.
The included features are:
– Persistent Footholds:
Eliminate hackers who are hiding in plain sight on Windows and Mac devices while plotting their next attack and give them a taste of their own medicine.
Today’s hackers are getting smarter. To evade detection, attackers are abusing legitimate applications and processes to slip through the back door undetected. Once inside, they establish a quiet foothold and plan their next move, often the deployment of malware to cripple systems, or ransomware to encrypt and steal sensitive data.
Huntress detects these persistence mechanisms to identify and eliminate persistent actors who are dwelling in your environments through unauthorized access. Protecting your customers from today’s clever attackers with custom incident reports, human-powered threat hunting and one-click approval of remediation steps.
– Ransomware Canaries:
Enable quicker ransomware detection and removal to reduce risk and maximize uptime.
– Managed Antivirus:
Reclaim existing investments in Microsoft Defender Antivirus and leverage Huntress to extend your front-end protection.
– External Recon:
Highlight external attack surfaces and expose easy entry points so you can strengthen defensive perimeters and improve your security posture.
– Process Insights:
Managed Endpoint Detection & Response (EDR) Backed by ThreatOps, visibility is Key to Advanced Threat Detection and Response.
– ThreatOps:
Move beyond automation with 24/7 human threat hunting, your secret weapon in the fight against today’s hackers.
– Partner Enablement:
Scale your cybersecurity practice with plug-and-play templates, threat landscape education and client-facing resources that help you capture new business.
4. Alert Logic
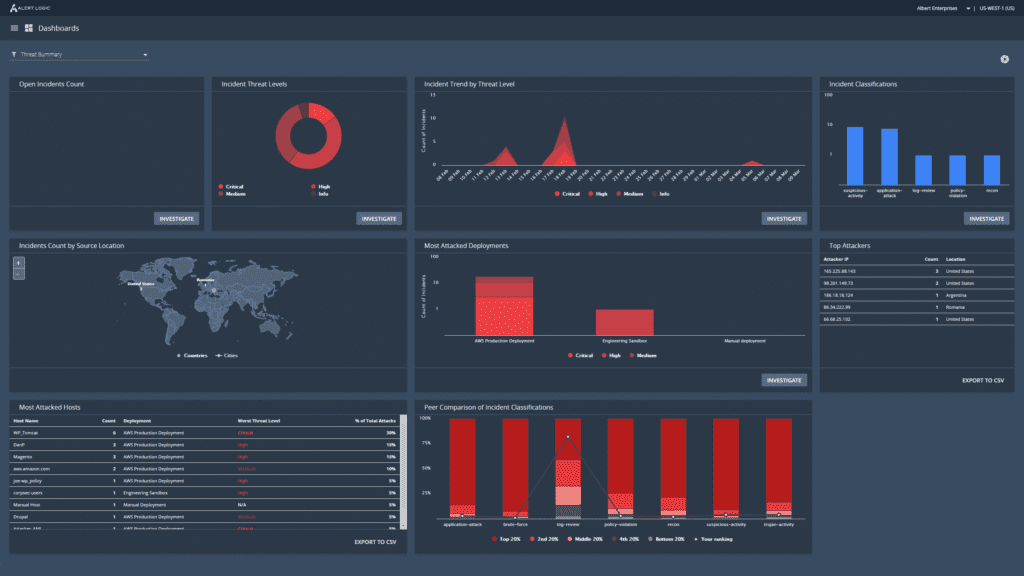
AlertLogic delivers white-glove managed detection and response service with comprehensive coverage for public clouds, SaaS, on-premises, and hybrid environments. Cybersecurity attacks are on the rise. Alert Logic MDR® gives organizations the tools and expertise to detect, respond to, and eliminate security issues in their systems and networks.
Comprehensive prevention and detection is at the heart of Alert Logic’s MDR solutions. It ensures all services are tailored to meet the specific cybersecurity requirements of your organization, so you’re best equipped to protect your critical systems from risk.
The core components of Alert Logic’s managed security services and solutions include:
– MDR FOR ANY ENVIRONMENT
Easily manage your cloud security posture with MDR solutions that run in all public, private, and hybrid cloud platforms.
– MDR FOR WEB APPLICATIONS
Continuous security monitoring and scanning of your application infrastructure to detect threats in real time and initiate appropriate responses.
– MDR FOR COMPLIANCE
Easily assess and implement security controls while preparing auditing reports fast, ensuring your organization is both audit-ready and compliant with all relevant regulations.
– MDR SOLUTIONS AND PRICING
Solutions tailored to match the security needs of all assets in your ecosystem, and priced accordingly.
Without accurate, real-time intelligence about the security incidents your organization experiences, it’s difficult to undertake appropriate response actions. Alert Logic’s security experts in the global Security Operations Center (SOC) aggregate information from thousands of customers using telemetry data, industry feeds, continuous research, and machine learning software to provide you with the most advanced threat intelligence.
MDR platform and expert services collect network traffic and more than 140 billion log messages every day, giving you outcome-based security coverage against all vulnerabilities and threats. Analyze and provide a curated set of content in a single location, so your organization can easily manage your security posture. Services that cover all your networks, applications, and endpoints, whether they’re in hybrid, on-premises, or cloud environments.
Alert Logic’s MDR platform provides a dashboard view of all alert information and analysis provided by a team of security experts. You get access to real-time information on risk, vulnerabilities, investigations, remediation activities, configuration exposures, and compliance status. Easily navigate the dashboard to rank your security threat priorities and focus your time and resources on threats that require more attention. Dashboards also provide user-friendly visualizations of risk to executive leadership teams.
What you can expect:
- A managed security solution that delivers the outcomes your organization demands
- An award-winning platform, cutting-edge threat intelligence, and expert defenders all working together for you
- 24/7 security operations and expert remediation advice
- Flexible coverage tailored to your individual business needs
- Simple pricing with a lower total cost than assembling and operating on your own
5. eSentire
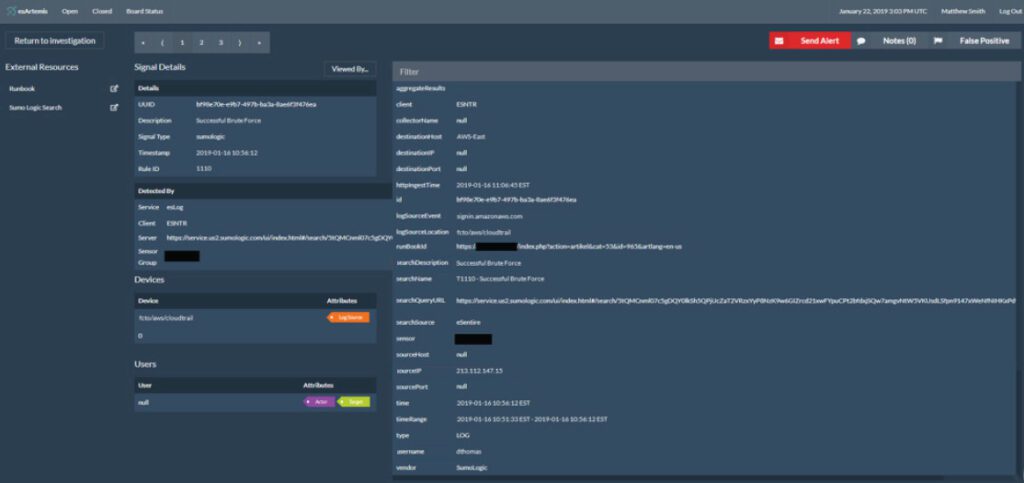
eSentire‘s complete, multi-signal Managed Detection and Response services provide 24/7 cutting-edge protection to prevent cybercriminals from ever disrupting your business.
Cyberattackers have the advantage. They only need to be right one time. With eSentire in your corner, you can outmaneuver even the most sophisticated attackers. Armed with unique intelligence and a complete picture of your attack surface, the Threat Response Unit, Elite Threat Hunters and 24/7 SOC Analysts are personally dedicated to protecting you and shutting down threats with potential to disrupt your business. It stays ahead of the innovation curve, so you can stay ahead of the threat curve.
eSentire Atlas XDR Cloud Platform provides a proactive security at scale to respond fast and mitigate business risk, you need complete visibility and coverage of your attack surface which uniquely delivers through a multi-signal approach to Managed Detection and Response. A powerful Atlas Extended Detection and Response (XDR) Platform ingests network, cloud, log, endpoint and insider threat signals, correlating indicators of compromise to detect, respond and automatically disrupt threats in minutes with a Mean Time to Contain of less than 15 minutes.
– Managed Vulnerability and Risk: Take control of cyber risk
eSentire offers multiple Managed Risk Services, tailored to your business needs, to help your organization proactively identify gaps, reduce cyber risk and continuously advance your security program. This includes a regular cadence of security assessments and testing to continue to strengthen your security posture.
– Managed Detection and Response: Prevent threats from becoming business disrupting events
The Managed Detection and Response service combines cutting-edge XDR technology, multi-signal threat intelligence and 24/7 Elite Threat Hunters to help you build a world-class security operation. The threat protection is unparalleled to see and stop attacks other providers and technologies miss, delivering the world’s most complete response capability.
– Digital Forensics and Incident Response: Be ready with the world’s fastest threat suppression
When you’ve been breached, every second counts so it provides 4-hour threat suppression, remotely, anywhere in the world with an On-Demand 24/7 Incident Response Retainer. The Digital Forensics and Incident Response (DFIR) services are also available as Emergency Incident Response support.
The Managed Detection and Response market is crowded with service providers and every company says the same thing. You need to learn how to separate MDR fact from fiction to select the right Managed Detection and Response provider to secure your business.
Use these MDR resources to quickly weed out fake MDR providers so you can build a more responsive cybersecurity operation today.
Put your business ahead of disruption:
- Recognized globally as the Authority in Managed Detection and Response
- The world’s most advanced XDR Cloud Platform
- 24/7 Threat Hunting & Disruption
- End-to-end cyber coverage and comprehensive services
- Team eSentire – Cyber Risk Advisor + SOC Cyber Analyst and Elite Threat Hunters on guard for your business 24/7
6. Crowdstrike
Crowdstrike‘s Falcon platform offers flexibility with better protection and performance. Secure your most critical areas of risk and stay ahead of today’s threats to stop breaches. With a real-time visibility, protect your business.
CrowdStrike protects the people, processes and technologies that drive modern enterprise. A single agent solution to stop breaches, ransomware, and cyber attacks powered by world-class security expertise and deep industry experience.
– Cloud native: Eliminates complexity and simplifies deployment to drive down operational costs.
– AI powered: Harnesses the power of big data and artificial intelligence to empower your team with instant visibility.
– Single agent: Delivers everything you need to stop breaches, providing maximum effectiveness on day one.
CrowdStrike pioneered a new approach to endpoint protection, designed and built to overcome the limitations of legacy security solutions. The Falcon platform delivers the foundation for true next-generation endpoint protection.
– 100% cloud-native.
The Falcon platform delivers immediate time-to-value, no hardware, additional software or configuration is required, which drives down cost and complexity.
CrowdStrike Security Cloud. The CrowdStrike Security Cloud is the brains behind the Falcon platform, providing complete real-time visibility and insight into everything happening on your endpoints throughout your environment.
– Single lightweight agent.
The intelligent, lightweight Falcon agent, unlike any other, blocks attacks while capturing and recording endpoint activity as it happens to detect threats fast.
– Protection for endpoints, cloud workloads and identities.
Enables frictionless endpoint, cloud workload and identity security, delivering real-time threat prevention and IT policy enforcement using identity, behavioral and risk analytics.
AI powered Machine Learning and IOAs protect against attacks:
- Protects against known and unknown , and malware-free or fileless attacks
- Combines the best NGAV prevention technologies such as machine learning, AI-powered indicators of attack (IOAs), high-performance memory scanning and more
- Eliminates ransomware
- Covers the gaps left by legacy AV
- Fully protects endpoints online and offline
- Cleans up known artifacts left behind from blocked malicious activity
7. Blackpoint Cyber
Blackpoint Cyber’s purpose-built MDR technology combines network visualization, tradecraft detection, and endpoint security to rapidly detect and neutralize lateral movement in its earliest stages. Faster than any other solution on the market, it harnesses metadata around suspicious events, hacker tradecraft, and remote privileged activity to stop advanced attacks immediately.
You have a critical mission: keeping your customers secure from threats. At Blackpoint, they built a robust cybersecurity ecosystem focused on effective threat detection and active response. The ecosystem ensures that all facets of security work in tandem to support an integrated, streamlined cyber strategy. Combining network visualization, tradecraft detection, and endpoint security, it detects and neutralizes cyberthreats in their preliminary stages to provide true, 24/7 defense.
Stay ahead of your cyber adversaries. Using nation-state-grade MDR technology, Blackpoint’s experienced analysts detect what others miss and take immediate action to secure your environment, with:
– True 24/7 MDR Working for You:
This nation-state-grade MDR platform powers the lean, pragmatic cybersecurity ecosystem protecting your business around the clock.
– Focus on Growing Your Business:
Trust the security expertise and competitively priced services to reduce your IT workload and prevent expensive, reputation-damaging breaches.
– Unrivaled Response:
Experienced SOC analysts leverage MDR technology and integrations to detect and actively respond to cyberthreats with industry-beating response times.
– The Pedigree Informs the Operations:
Founded by former national security experts, operates with deep knowledge of real-world cyber defense tactics and malicious tradecraft.
How it works:
– Monitor:
Blackpoint hunts proactively for evolving threats 24/7, maintaining full visibility of your entire network. The experienced team leverages leading-edge, proprietary technology to monitor for indicators of compromise, malicious behavior, and open risks.
– Detect:
Every second counts when it comes to detecting the first signs of breach. Blackpoint detects and isolates developing threats before they can spread laterally. It investigates suspicious activity on your behalf and eliminate alert fatigue and time spent on false positives.
– Respond:
In the fastest responses times seen by the industry, Blackpoint isolates and stops malicious processes. It takes action to neutralize threats in real-time rather than sending you instructions to action yourself. Get alerted after the risk is eliminated and we’ve secured your environment.
8. Expel
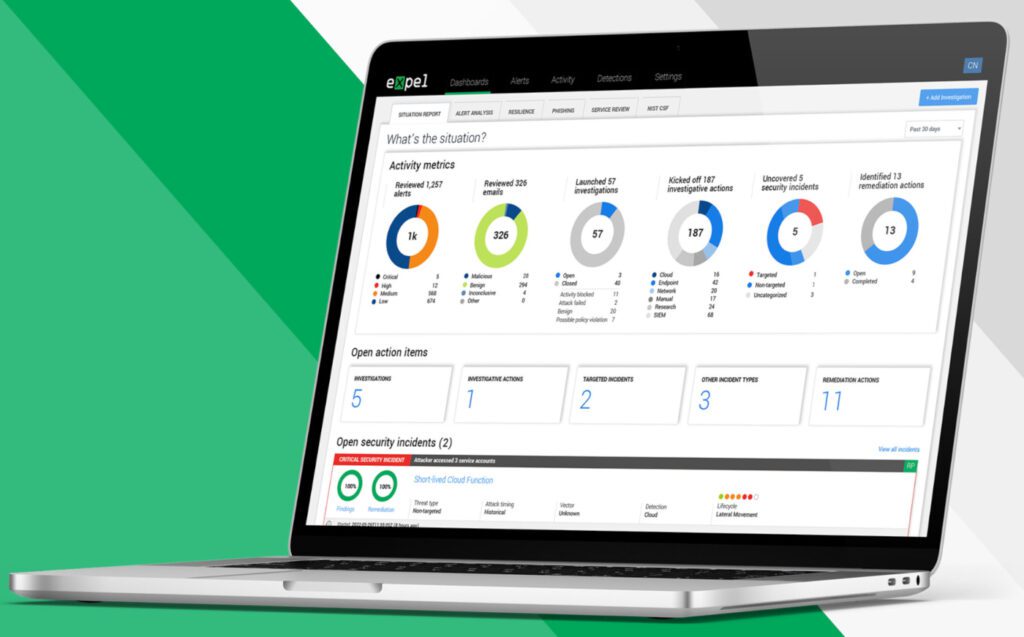
Expel is a recognized leader in managed detection & response. When it spots a critical attacks, it can go from alert to triage in less than 3 min. You can choose to protect everything from cloud infrastructure, on-prem infrastructure, SaaS apps, or just what you need. This unique MDR approach includes extended detection and response (XDR) capabilities to give you a full picture across your security and business applications. And with the SOC analysts chasing down your alerts and responding to incidents 24×7, your team can focus on advancing security strategies unique to your business.
– Detect: It applies an additional layer of security with custom rules.
– Investigate and respond: It finds out exactly what happened and tells you what to do about it.
– Remediate: It will automatically contain hosts in your environment.
– Hunt for threats: It proactively looks for threats on-prem and the cloud.
In case you are you looking to protect:
– Cloud infrastructure:
If you’ve moved to the cloud, we’ll connect to your AWS, Azure or GCP environment to identify: data loss, compromised accounts, web application attacks, misconfigurations.
It will let you know when it discovers anomalous activity, the investigative details and next steps to fix it.
Examples of unique things it monitors for AWS cloud service suspicious or unusual activity:
- Suspicious commands via AWS SSM
- Deleted or disabled CloudTrail or GuardDuty
- AWS EC2 credential compromise
- Publicly accessible S3 buckets
- Suspicious AWS CloudWatch event rule creation
- Unauthorized resource sharing
- Use of lambda to backdoor AWS accounts
– On-prem infrastructure:
BYO-tech MDR that shrinks alert-to-fix timelines, the analysts (and bots) triage the alerts from your security tech. When it finds something suspicious, you’ll know right away. Plus. it can automatically contain the threat so you get the space to breathe during an incident.
– SaaS apps:
It looks at user behavior in your applications like Microsoft O365 and Okta to search for: unusual user behavior, compromised accounts, data loss, privileged access abuse.
9. Cyrebro
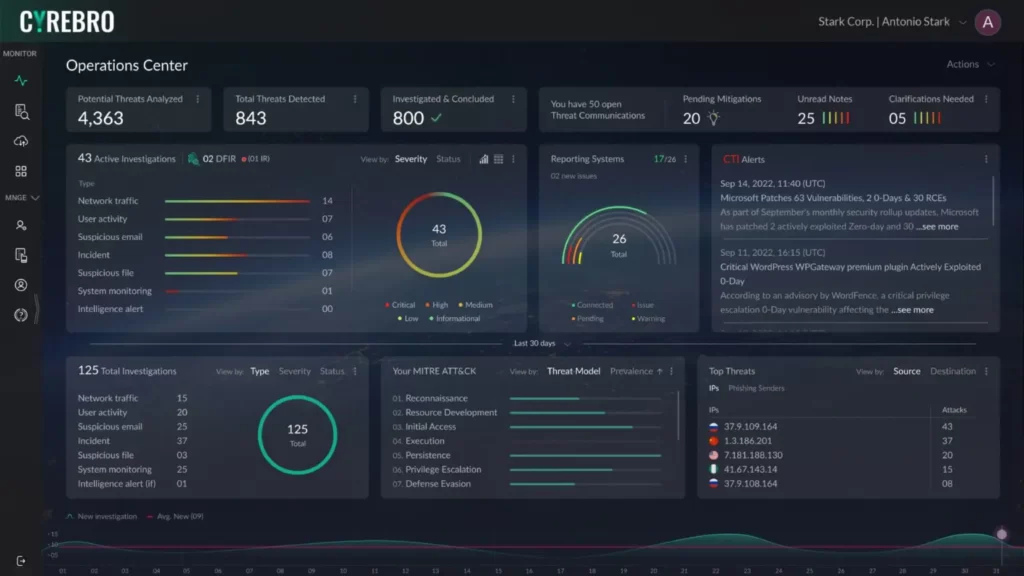
Cyrebro is the core of your company’s cybersecurity, providing a first-of-its-kind managed SOC Infrastructure. You are secured with enterprise-grade security no matter the size of your business; ensuring fast and effective incident response, 24/7/365 monitoring, mitigation of cyber threats, and proactive threat intelligence.
Your company automatically benefits from the collective wisdom derived from the data lake. All intelligence conclusions gathered from previously resolved incidents are collected and automatically fed directly into your security defense for enhanced protection. Threat hunting is ongoing based on queries created by CYREBRO’s research team. We’re constantly uncovering new threats using known IOCs and the latest TTPs combined with advanced analytics and machine learning algorithms.
Understand emerging threats. Stop them in their tracks. Empower your business by having the most sophisticated threat intelligence team on your side, working for you to track, analyze and develop proactive tactics to respond to continuously evolving cybersecurity incidents.
The intelligence team becomes yours, fighting emerging cyber threats requires more than defensive actions. You need a solution that incorporates the ongoing and in-depth work of threat intelligence analysts to identify susceptibilities and neutralize threats before they penetrate systems.
– Proactive strategies:
The threat intelligence analysts sift through hundreds of data streams and alerts to develop a deep understanding of threat behaviors and TTPs which are then translated into proactive plans and SIEM rules to mitigate potential attacks.
– Create context and correlations:
By enriching and contextualizing alerts with real-world research, analysts can reveal a threat actor’s motivations and methods, providing actionable guidance for incident response and preventing future attacks.
– Data-driven decision making:
Make faster, knowledge-backed security decisions with confidence, knowing that they are supported by in-depth analysis and a SOC solution that has already addressed them. What Cyrebro grants you is:
– Full Visibility: Connecting to all of your security technologies in one place, see all your security events and what they mean with complete clarity and prioritization.
– Cyber Brain: Proprietary detection algorithms strategically monitor, analyze and interpret consequences of events across all your security solutions and business environments.
– Interactive Platform: Actionable mitigation steps inside the platform so you can make smart decisions whether you’re securing one business or many.
10. Heimdal
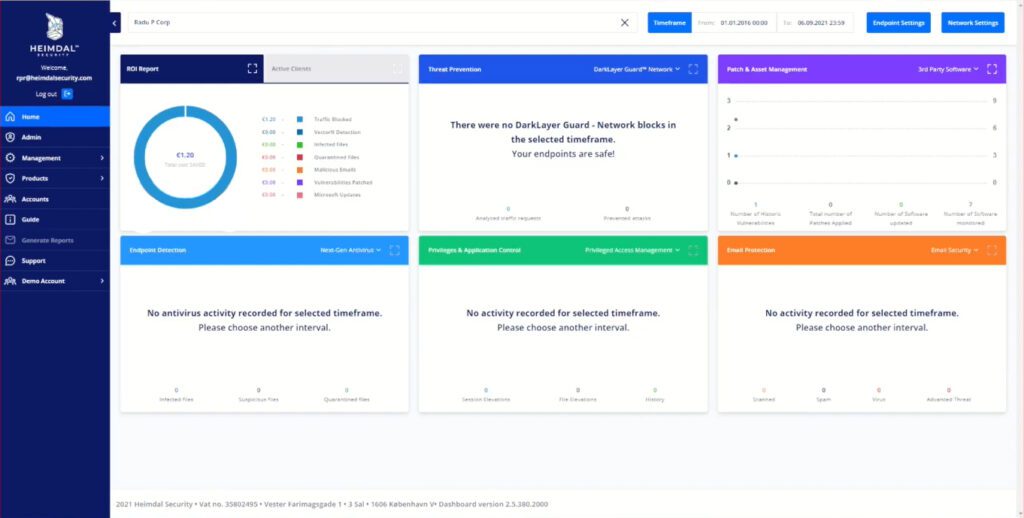
Let Heimdal monitor your environment, the Extended Detection and Response team will alert you on infection or attack, validate policy checking for maximum compliance, and employ rapid and decisive responses to attacks.
Heimdal is an environment security outsourcing made simple. With indication, detection, analysis, responseand and remediation:
– Simplified Data Gathering:
Data gathered from across your ecosystem is fed into Heimdal’s Intelligence Center for fewer false positives and rapid and accurate detection.
– Greater ops, fewer costs:
XDR’s fully automatic functionality allows for greater incident and response operations while keeping down the costs.
– Monitor devices across complex business environments:
XDR allows you to establish contextual relationships between your business assets (endpoints, email, networks, servers, cloud) to offer a clear-cut overview.
A unique solution for advanced problems, with those key benefits:
– Bringing the decisive, move to hackers: Heimdal employs a rapid and decisive response to attacks and attackers, by supplying you with extended, systemized reports on potential risks, online threats, and vulnerabilities.
– Superior Protection: Heimdal’s XDR replaces fragmented, legacy tools and unresponsive data-gathering software for a consolidated approach, offering you a seamless user experience and ease of mind.
– Much more than technical support: XDR offers much more than traditional technical support, detailed incident reporting, actionable remediation items, disaster recovery plans, and advanced detection approaches.
Discover the award-winning solutions from Heimdal Security for proactive protection with a market-leading detection rate, unified in one fully compliant cybersecurity suite. Prevent, detect, and respond to any threat painlessly, while at the same time defending your avenues of digital communications against outside threats.
Mitigate threats on the inside and achieve compliance with international standards in the process by managing privileges and applications, as well as offer your employees and customers support when they require it, all in one place. The Heimdal Unified Dashboard makes cybersecurity simple with an accessible interface and stunning reports that are easy to read and use.
The remote access and support solution allows you to connect with your employees and customers across various devices without any difficulty. Fully compatible with Windows, Mac, and Android. Heimdal™ Remote Desktop Secure comes with stunning visuals and stable session quality. Compliant and ready-to-use, it is the finishing touch to add to complete your suite of cybersecurity solutions.
Conclusion
To sum things up, it’s important to acknowledge that Managed Detection and Response enables an organization to reveal cybersecurity risks, monitor them, and estimate how much exposure they result in.
It gives an organization the necessary defense for dealing with advanced threats and provides security teams with the tools they require to deal with these threats.





