10 Best Cloud Access Security Broker (CASB) Software
As businesses increasingly adopt cloud-based applications and services, ensuring security for sensitive data and maintaining regulatory compliance have become top priorities. Cloud Access Security Brokers (CASBs) play a crucial role by providing enhanced visibility, data protection, and threat prevention across cloud environments. CASBs help organizations monitor and control cloud activities, safeguard data, and prevent unauthorized access. Here, we’ve compiled a list of the 10 best CASB solutions available, each offering unique features and benefits tailored to meet various enterprise security needs.
Top 10 Software
10 Best Cloud Access Security Broker (CASB) Software ?
1. Check Point
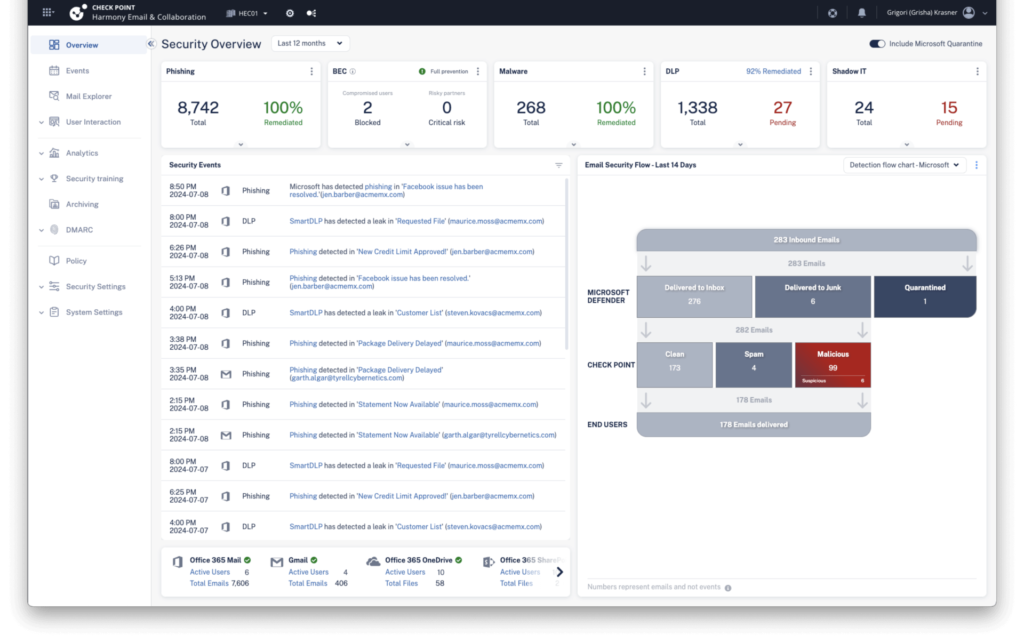
Check Point’s Harmony Email & Collaboration Security offers a dedicated approach to protecting cloud collaboration tools like Microsoft 365 and Google Workspace. Leveraging AI, it detects and prevents advanced threats, including phishing and account takeovers. With built-in data loss prevention (DLP) capabilities, Harmony protects sensitive information and aids in compliance with stringent data regulations. This solution is particularly well-suited for organizations that rely heavily on email and collaboration apps in their cloud environments, providing robust, real-time security and visibility.
2. Netskope
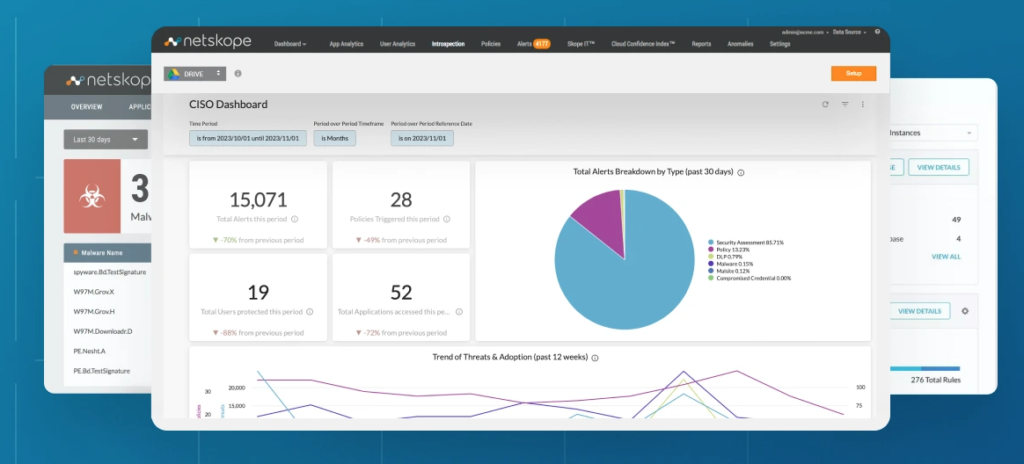
Netskope’s CASB is part of its comprehensive Secure Access Service Edge (SASE) platform, designed to secure data in real-time across cloud, SaaS, and web applications. It offers a Zero Trust model, advanced threat detection, and policy enforcement to secure data regardless of user location. By providing deep insights into user behavior and cloud activity, Netskope enables organizations to enforce access controls and prevent unauthorized data sharing. Netskope’s solution is ideal for enterprises seeking flexible, scalable security to protect cloud and hybrid work environments.
3. Trendmicro
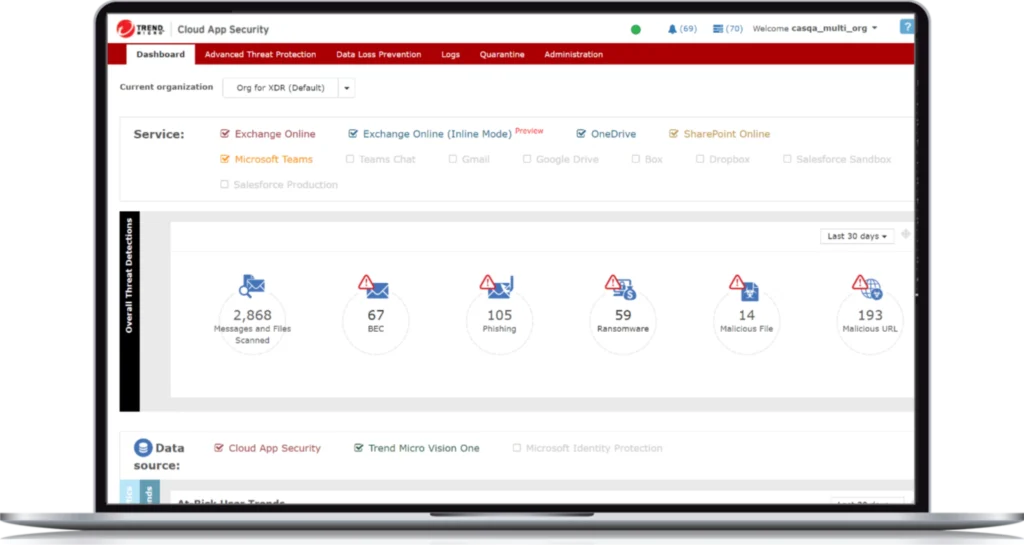
Trend Micro’s Cloud App Security provides seamless integration with leading cloud platforms like Microsoft 365, Google Workspace, and Dropbox. It enhances threat detection with anti-phishing, malware detection, and advanced DLP features, which help guard sensitive information in email and collaboration tools. This CASB solution also enables granular access control, giving organizations deeper insight into data usage and enforcing policies to prevent unauthorized data sharing.
4. Broadcom
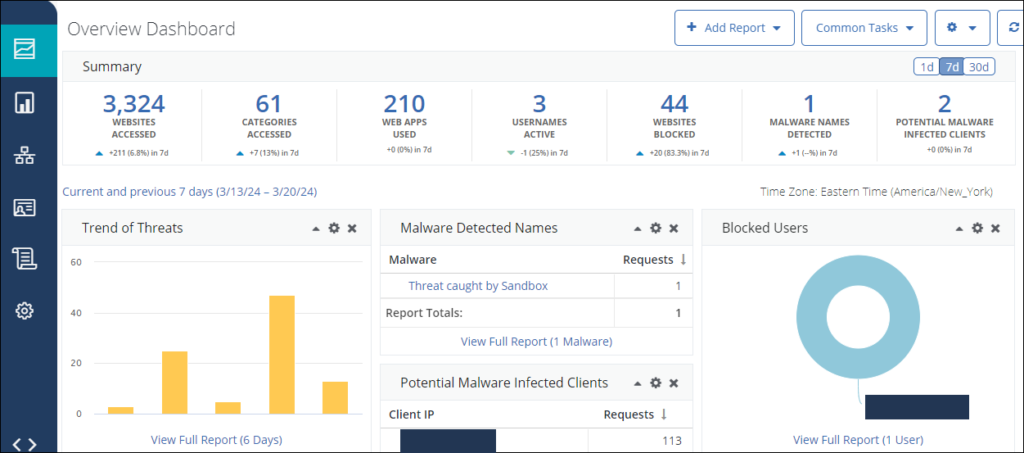
Broadcom’s Cloud Secure Web Gateway combines CASB functionalities with robust web protection. It enables secure web access while protecting cloud applications through web filtering, DLP, and threat defense. Its focus on compliance, real-time threat response, and monitoring of user activities across cloud applications makes it ideal for large organizations aiming to manage cloud security while maintaining regulatory standards.
5. Oracle
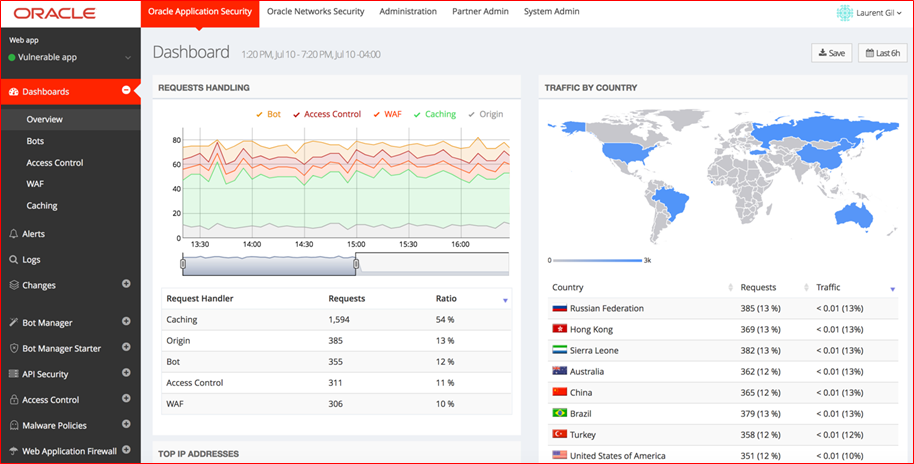
Oracle Cloud Security offers a comprehensive approach to cloud security, integrating CASB capabilities with Oracle’s cloud infrastructure. It includes machine-learning-based anomaly detection, secure access management, and extensive encryption features. This CASB solution supports regulatory compliance across multiple industries, making it particularly useful for enterprises that rely on Oracle’s suite of cloud products.
6. Forcepoint
Forcepoint ONE integrates CASB, DLP, and secure web gateway features, providing an all-in-one platform for cloud security. With its policy-driven approach, Forcepoint enables organizations to protect sensitive data across all cloud applications and collaboration tools. Real-time monitoring, advanced threat protection, and granular access control are central to Forcepoint’s solution, making it highly suited for industries that require flexible data protection across diverse cloud environments.
7. Managed Methods
Managed Methods stands out as a CASB tailored for smaller organizations and K-12 schools, providing straightforward security for Google Workspace and Microsoft 365. This solution offers data protection, malware detection, and compliance tools, making it accessible for institutions with limited security resources. ManagedMethods is ideal for organizations seeking an affordable yet effective way to protect sensitive data and prevent unauthorized access in cloud-based educational and professional environments.

8. SkyHigh Security
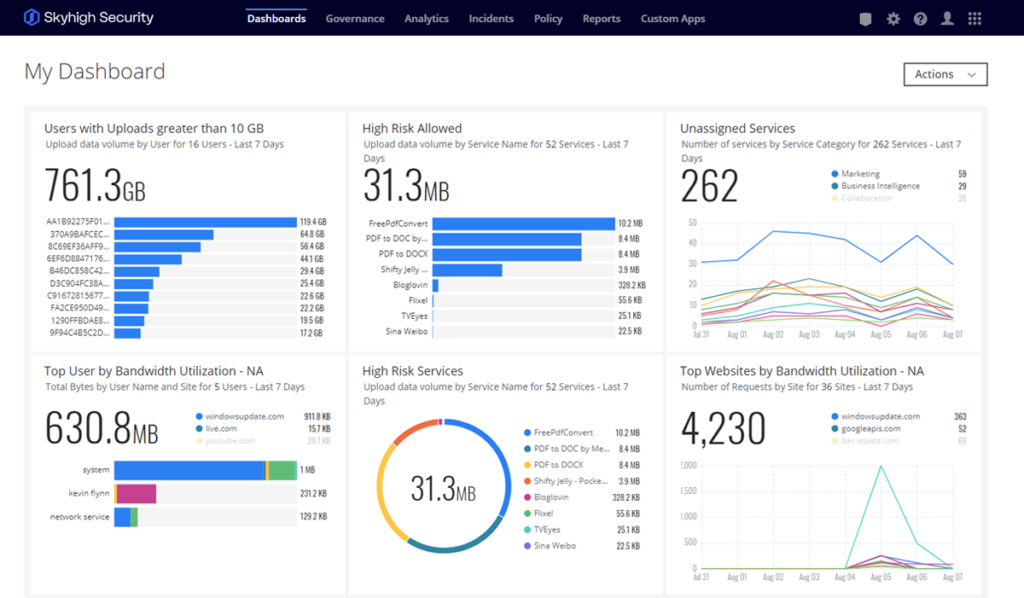
Skyhigh Security offers a robust CASB solution with a focus on real-time threat protection, policy enforcement, and data governance. Previously part of McAfee, Skyhigh enables organizations to enforce security policies across SaaS applications, monitoring user activity to prevent data leaks and respond to threats. With its strong DLP and access control features, it’s well-suited for businesses requiring detailed cloud usage insights and security policy enforcement.
9. Proofpoint
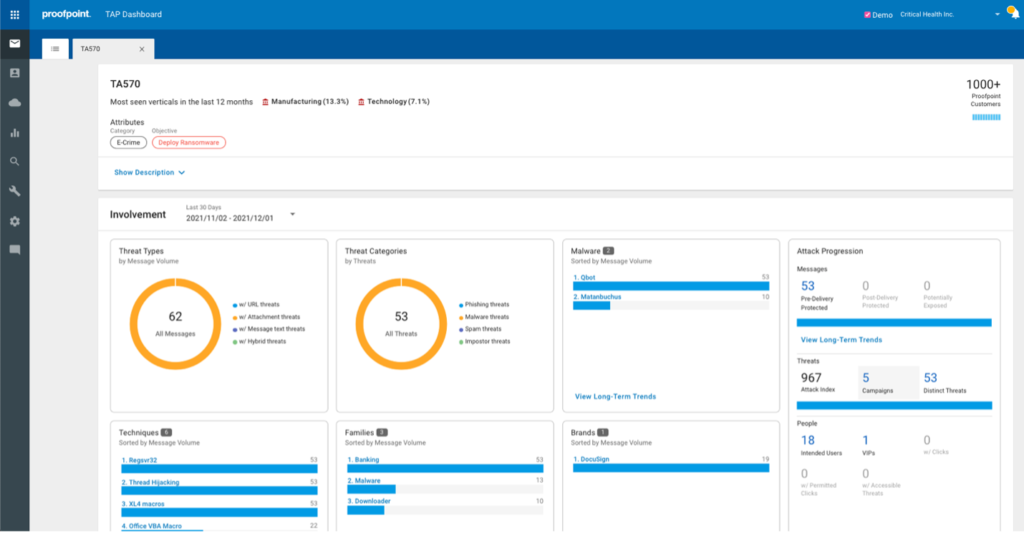
Proofpoint’s CASB is designed for data security, particularly in email and collaboration platforms. It provides data loss prevention (DLP), advanced threat protection, and detailed monitoring of cloud activity, enabling administrators to control access and data sharing. This solution is ideal for businesses looking to protect sensitive information and ensure compliance, especially those with heavy email usage or regulatory requirements.
10. McAfee
McAfee MVISION Cloud offers comprehensive CASB features with strong DLP, threat detection, and access management. Its analytics engine detects risky behavior and security incidents, allowing organizations to protect data across multiple cloud applications. MVISION is especially effective for large enterprises looking for a scalable CASB solution that can safeguard sensitive data and enforce security policies across extensive cloud infrastructures.

Conclusion
Selecting the right CASB solution depends on the specific security requirements and the cloud environments of your organization. From comprehensive threat detection to compliance and data protection, each CASB on this list offers robust capabilities to secure cloud assets. By adopting a CASB, organizations can manage risks, enhance visibility, and ensure compliance as they transition to the cloud, fostering a secure digital environment for their operations.





