10 Best Threat Intelligence Software and Platform
You want a solution that enables your security team to be proactive when it comes to defending your critical assets but also help you to achieve full situational awareness so you will always know:
When you have been attacked?
Is there a new potential attack on the rise?
Who is the target within your organisation? Why?
What vulnerabilities the attackers are planning to exploit?

DataMinr
Good for business starter

Authentic8
Good For business

CrowdSec
Best for medium business
A Threat Intelligence Software and Platform is what will give answers to the previous questions. Here is a list of 10 software that you can choose from.
Top 10 Software
1. Dataminr
Dataminr is an event and risk detection, Dataminr’s real-time AI platform detects the earliest signals of high-impact events and emerging risks from within publicly available data, plus rich visual context and tools that help you collaborate and act faster—so you can better protect your people, brand and physical and digital assets. Know critical information first, respond with confidence and manage crises more effectively.
Dataminr has been pioneering AI/ML systems for real-time event detection since 2010, whith the first Natural Language Processing and Machine Learning patent for detecting events in micro blogs. The team of data scientists, engineers, and researchers use a range of Deep Learning AI methods from a number of scientific fields, ranging from Natural Language Processing, Natural Language Understanding, Natural Language Generation, Computer Vision, Audio Processing and Classification, and Anomaly Detection on both Machine and Human-Generated Public Data Streams.
Learn how Dataminr delivers real-time alerts that enable businesses to stay ahead of risks and operate more resiliently:
– Discover: Know First, Act Faster
Dataminr Pulse provides the fastest, most relevant alerts on emerging risks across the world. The AI platform cross-correlates more than 500,000 public data sources—including first-hand accounts, audio transmissions, the deep and dark web and IoT sensors—to provide comprehensive, real-time event detection.
– Contextualize: Connect the Dots and Respond With Confidence
Visualize real-time information at the level and specificity needed to quickly contextualize, understand and respond to high-impact events as they unfold with Dataminr Pulse’s advanced geovisualization capabilities.
– Collaborate: Effectively Operationalize Real-time Information
Dataminr Pulse streamlines your team’s collaboration, response protocols and critical information flows—enabling real-time command and control as physical and cyber risks emerge and high-impact events unfold.
Discover the Dataminr Advantage:
– Leader: According to user reviews, 90% of Dataminr users were likely to recommend it—leading to high ratings overall and high market presence scores.
– Easiest To Do Business With: Customers gave Dataminr a 10/10 rating based on their satisfaction, trust and the product’s convenience.
– Momentum Leader: Dataminr was ranked among the top 25% of products in operational risk management by G2 users.
– Best Support | Enterprise: Dataminr’s support was rated 9.8/10 based on reviews by verified consumers on the quality of support and ease of doing business.
– Users Love It: Over 94% of 41 user reviews scored Dataminr 4/5 or 5/5 stars.
2. Authentic8
Authentic8‘s Silo secures and anonymizes online investigations for gathering threat and cybersecurity intelligence. Silo shifts your risk to an isolated cloud-native environment that you control. Silo can be configured specifically to meet your most demanding requirements.
The Silo Web Isolation Platform is a secure, cloud-native execution environment for all web-based activity. Silo is built on the principles that all web code and critical data should be isolated from the endpoint, and that browsing capabilities should be configurable and auditable — like any other enterprise workflow.
This platform capabilities are:
– Seamless deployment:
A cloud-based solution that deploys in seconds — whether it’s for a single user or thousands. Silo doesn’t require infrastructure investment; its ability to easily scale lets IT focus on solving business problems, not managing procurement. And Silo can be used as a standalone native app, integrated with a browser or incorporated into any workflow using APIs, allowing IT to define a specific experience for users.
Unlike more traditional security solutions that require synchronizing software across endpoints, integrating with network infrastructure and piping disaggregated logs into a unified system, Silo lets you deploy across your user population with a click of a button. Silo can scale up and down as your needs change, allowing you to deliver the right solutions for your users at the right time.
– Role-based provisioning
Patented user/group and policy framework ends the tyranny of one-size-fits-all. Silo lets you define access, authentication and use policies across computers, locations and web resources. Whether you want a throwaway browser for personal use or a locked-down environment for a sensitive workflow, Silo gives IT unprecedented control over how the web is used.
Silo can be tuned to meet the fluid needs of your organization. Define policies centrally and rest assured that they follow the user across devices and locations.
– Integrates with IT services
From directory services to identity management platforms, secure web gateways and SIEM solutions, Silo plays nicely with your current IT technology stack. Conversely, Silo can also act as a completely standalone environment, giving you the power to choose how Silo will work best for your organization.
Silo can provide a standalone user experience and execute completely outside of your organization’s infrastructure. Or it can be woven into current IT solutions and the local browser for seamless remote access to corporate resources. Silo matches your organizational structure as defined in your on-premises directory service. If you’re using an identity management platform, third-party SAML or other cross-authentication solutions, they can be used to authenticate users when they access Silo, and they can be used for single-click access to provisioned web applications.
– Global certification standards
Silo meets the needs of the most regulated organizations in the world, from federal agencies to Swiss banks to healthcare providers. All data is encrypted and protected to the highest standards. And Authentic8 undergoes regular third-party audits and assessments to remain compliant with FedRAMP, PCI, HIPAA, SOC2 and more global standards.
Platform security is an intrinsic value at Authentic8. Whether pursuing the compliance with global security standards like NIST and ISO, meeting specific industry requirements or delivering a solution to help you meet compliance requirements, Silo is built from the ground up with information security in mind. With SIlo, you control how much customer-identifying information is stored in the system. Silo encrypts log data with keys managed by the customer, and it provides APIs to extract and pipe data into third-party analysis tools. It also provides APIs to extract your data should you decide to stop using the service.
3. Crowdsec
Crowdsec CTI one of The Best Threat Intelligence Software and Platform, is a collaborative cyber threat intelligence platform providing real-life and highly curated data on IP reputation, helping cybersecurity experts to better assess threats and fight back more efficiently.
CrowdSec cyber threat intelligence tools are the largest community-fueled CTI network on earth, CrowdSec CTI distributes IP reputation intelligence, allowing SOC teams & security analysts to obtain highly curated data on intrusion attempts, origins, and trends.
– Understand your attackers: Strictly curated data sets
Most CTI solutions are crippled by low data quality. False positives, deprecated data or poisoned bases increase alert fatigue and provide unreliable information to make decisions. CrowdSec CTI is curated to make sure only high-confidence data is shared with the users.
-Each contributing user gets a reputation score based on seniority and contribution. The higher the reputation, the higher the value the curation algorithm will give to the data provided by the user
-CrowdSec operates its own network of honeypots. User data is correlated with data from honeypots to ensure homogeneity.
-The Smoke database exposes non-curated data to enrich SOC teams or analyst data
-The Fire database provides curated data for direct ingestion by firewalls to preventively block aggressive IPs.
– Two databases: of Highly accurate and detailed information
CrowdSec users share millions of signals daily, allowing us to gather a large amount of information on each IP address.
-Each IP address shared gives us information on the type of attack, moment and use case, allowing us to assess its aggressivity of each IP address.
-CrowdSec enriches that data with third-party resources to add information such as country of origin, autonomous system etc.
-Reputation data is frequently refreshed to make sure it reflects the lifecycle of an IP address.
– Supercharge the existing: Strictly curated data sets
Most CTI solutions are crippled by low data quality. False positives, deprecated data or poisoned bases increase alert fatigue and provide unreliable information to make decisions. CrowdSec CTI is curated to make sure only high-confidence data is shared with the users.
-Each contributing user gets a reputation score based on seniority and contribution. The higher the reputation, the higher the value the curation algorithm will give to the data provided by the user
-CrowdSec operates its own network of honeypots. User data is correlated with data from honeypots to ensure homogeneity.
-The Smoke database exposes non-curated data to enrich SOC teams or analyst data
-The Fire database provides curated data for direct ingestion by firewalls to preventively block aggressive IPs.
– Use the API: Seamless integration with your cybersecurity solution
CrowdSec CTI was designed to seamlessly interface with most cybersecurity solutions.
-Individual queries on IP addresses can be done through a dedicated UI in CrowdSec Console, or directly through an API.
-CrowdSec CTI can stream IP blocklists directly to any firewall or remediation solution. Whether you use Palo Alto or OPNSense, your solution will consume IP data to provide preventive defense.
-Full bulk lists of IP data can also be purchased for data analysts or to train AI models.
Why you would choose CrowdSec is beacause Cybercriminals need IP addresses to mask their locations. CrowdSec is a platform federating blue teams to secureall Internet-exposed infrastructures.
4. Logpoint
The Logpoint SIEM & SOAR threat intelligence application offers a simple and efficient advanced threat intelligence platform. Empower your security analysts with SIEM & SOAR Threat Intelligence
The key to advanced threat detection is to understand your vulnerabilities and to have adequate experience and intelligence to mitigate threats. While indicators of real risk are often difficult to identify and preparation to each and every new threat is impossible, making the best use out of available intelligence sources will help your organisation to prioritise threats and broaden your armoury should it come down to an attack.
Threat intelligence automation, one aspect of a holistic cybersecurity strategy, helps you comprehend risks related to the most common and severe external threats, such as zero-day threats, advanced persistent threats and exploits. It enables you to collect and analyze data on the latest threats from a wide range of sources. Threat intelligence information from security vendors, intelligence groups and connections to your own network helps you fend off attacks by initiating security activities to stop malicious behavior and avoid incidents.
Threat Intelligence automation is an aspect of cybersecurity that no-one in charge of a network can afford to ignore. Its role in network defense is now proven, and the threat data collected has an indisputable value for organizations. In effect, they give decision-makers a reliable basis to help confirm the benefits and consequences of their decisions.
Being proactive is key:
Real-time feeds combine intelligence and previous experience from other organizations into a single source providing your team with contextual information to make better informed strategic choices and therefore mitigate attacks.
However, identifying a threat within large volumes of collected information could be like finding a needle in a haystack. You may find yourself asking:
What am I looking for?
How can I differentiate normal and malicious activity that might signal an attack?
The reason why the integration of SIEM, SOAR and TI is regarded as a two-bladed sword by some lays in the lack of calibration. In Logpoint, it’s not the volume of information but the right implementation is what leads to results.
While ongoing analysis of enterprise log data alone is valuable, next-gen protection against advanced threats is only possible by comparing your internal datawith the relevant indicators of compromise. By optimizing your internal data with the threats your sector is the most exposed to, Logpoint SIEM & SOAR integrated with TI feeds together creates a highly focused solution to gain the most insights out of your enterprise log-data for maximum efficiency.
Integration of SIEM, SOAR and Threat Intelligence brings customers even faster threat correlation and management to enhance their ability to monitor, manage and remediate cyberthreats. Leveraging Logpoint’s architecture, organizations can now benefit from an accelerated ability to correlate multiple threat indicators generated inside their perimeter with external threat IOCs.
5. Lookout
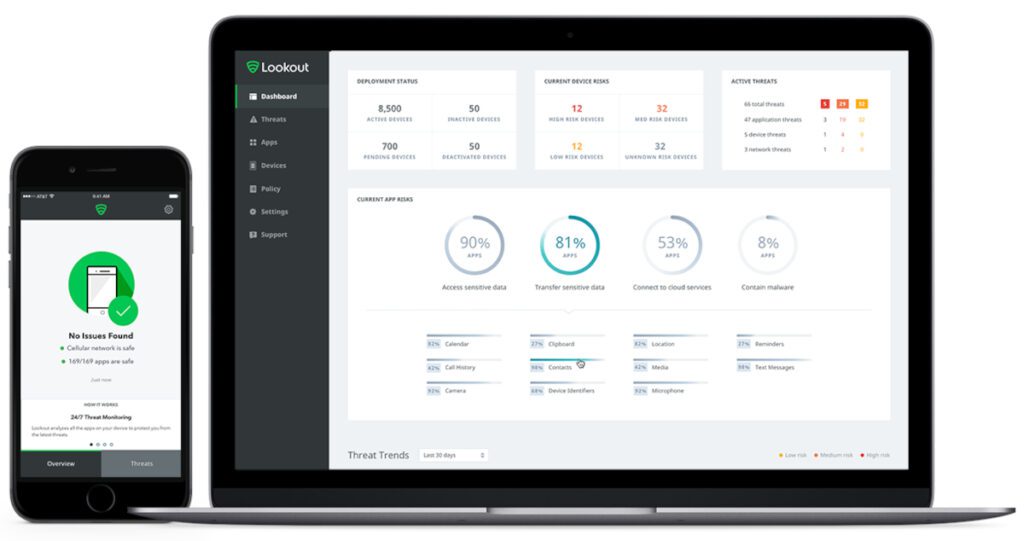
Lookout Threat Advisory provides cutting-edge mobile threat intelligence from Lookout’s global sensor network of millions of mobile devices and insights from Lookout’s top mobile security researchers. Customers get access to monthly threat reports and analyst inquiry calls, quarterly webcasts, and also get early access to novel Lookout threat research.
In the fast-changing world of mobile security, keeping your finger on the pulse can be challenging. Lookout Threat Advisory taps into the massive dataset from Lookout’s global sensor network of millions of devices, pairing it with insight from its top security researchers to give you actionable intelligence on the latest mobile threats and risks.
What you get using this platform:
Lookout Threat Advisory provides you with a regular cadence of threat intelligent updates and analyses, as well as direct access to the leading mobile security researchers in the world.
– Monthly global threat report
Every month you’ll receive a detailed report containing the latest threat encounter rates, trends, and top threat families
globally.
– Five monthly analyst inquiries
Schedule up to five, one-hour threat inquiry calls every month with Lookout’s industry-leading threat analysts.
– Periodic threat webcast
Tune in for exclusive webcasts where Lookout’s top researchers will recap key quarterly trends and discoveries.
– Early access to new threat research
Receive two-week advance copies of Lookout’s latest novel threat discovery reports.
The first step of securing data is knowing what’s going on. It’s hard to see the risks you’re up against when your users are everywhere, using networks you don’t control to access your data in the cloud. The Lookout SSE solution eliminates the guesswork by providing visibility into what’s happening, on both unmanaged and managed endpoints, in the cloud and everywhere in between.
Lookout analyzes behaviors to detect insider threats and file-less cyberattacks. It protects your users from malicious content and classifies your sensitive data on the fly. It also continuously monitors the risk level of your endpoints and dynamically modifies user access to protect your data.
The Lookout security policy engine is unified and easy to use. With a single place to monitor risk and enforce security policies, you can protect your data from external threats, insider threats or accidental data leakage.
The Lookout Security Platform cross references user behavior, endpoint risk posture and data sensitivity to adjust access policies in real time. You can enable the modern workforce without putting your data at risk.
6. Cisco
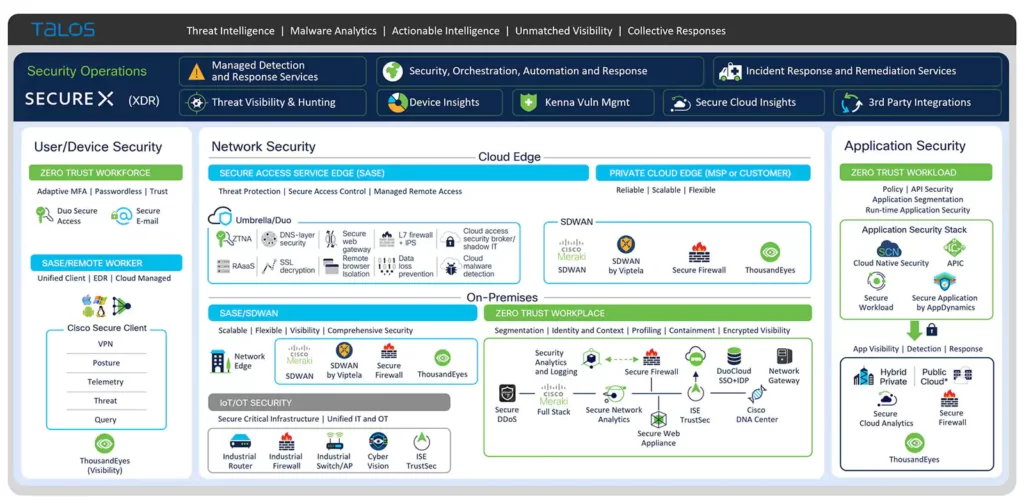
Cisco Talos Intelligence Group is one of the largest commercial threat intelligence teams in the world, comprised of world-class researchers, analysts and engineers.
These teams are supported by unrivaled telemetry and sophisticated systems to create accurate, rapid and actionable threat intelligence for Cisco customers, products and services.
Talos defends Cisco customers against known and emerging threats, discovers new vulnerabilities in common software, and interdicts threats in the wild before they can further harm the internet at large.
Talos maintains the official rule sets of Snort.org, ClamAV, and SpamCop, in addition to releasing many open-source research and analysis tools.
– To stop more, you have to see more
– Rapid analysis for greater threat context
– See once, protect everywhere
To keep your business resilient in the face of attacks, the Cisco Talos Incident Response service uses global threat intelligence research and the largest telemetry and partner network in the industry.
A Comprehensive Threat Intelligence:
Talos was formed by combining SourceFire’s Vulnerability Research Team, the Cisco Threat Research and Communications group, and the Cisco Secure Applications Group.
The combined expertise is backed by a sophisticated infrastructure, and Cisco’s unrivaled telemetry of data that spans across networks, endpoints, cloud environments, virtual systems, and daily web and email traffic.
Fostering an Informed Community:
Talos utilizes its extensive threat intelligence to make the internet safer for everyone.
A variety of free software, services, resources and data are available to the public, including official rule sets and communities.
Additionally, Talos promotes an informed security community, posting information on new threats and research on the Talos Blog, ThreatSource newsletter, social media, and on the Beers with Talos podcast, with new episodes posted biweekly.
7. ActivTrak
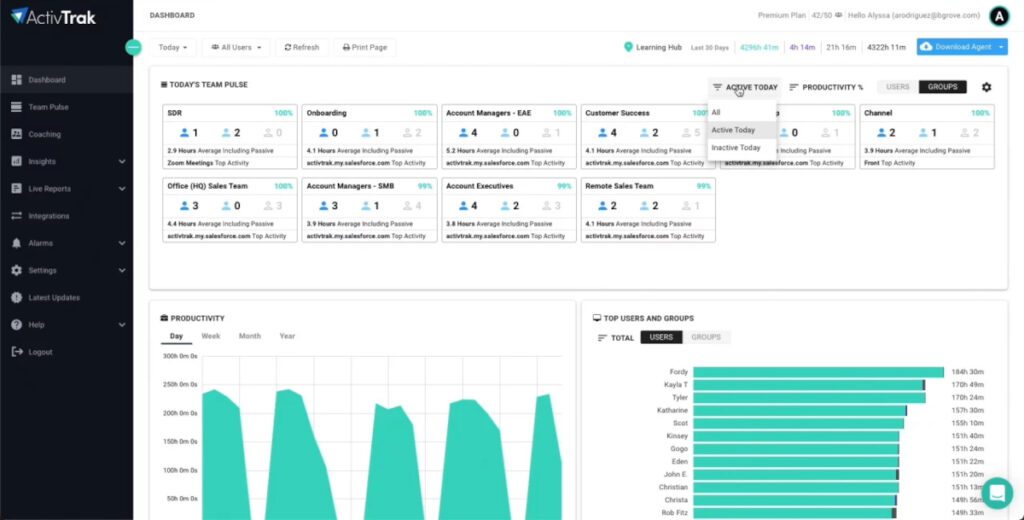
ActivTrak one of the Best Threat Intelligence Software and Platform, is an easy-to-install, low-maintenance insider threat detection solution. It’s continuously tracking and reacting for you, freeing up your time to focus on securing other areas of your environment. ActivTrak’s comprehensive approach to insider threat management ensures that administrators have the information they need to prevent and detect insider threats.
In the world of cybersecurity today insider threats are a hot topic of conversation, and for good reason. Research conducted by Crowd Research Partners and Cybersecurity Insiders found that 90% of organizations feel vulnerable to insider attacks for multiple reasons that include an ever-changing landscape of technology and devices as well as excessive access privileges and other factors. Moreover, 53% of companies confirmed insider attacks against their organization.
With security breaches increasing by an average of 27.4% year over year, the emphasis on Insiders is well placed.
An Insider threat is a person within an organization that presents a threat of being the root cause or entry point for a data breach. Any person that gives an opportunity for a malicious individual to gain privileged access to sensitive information held by an organization using sources within that organization for lateral movement throughout a company network is considered an insider threat.
Many people have access to an organization’s network including current and former employees, contractors, vendors and more. This means the sheer number of potential threats make threat detection incredibly difficult to track and identify before an attack occurs.Insider threats can be grouped into three main categories:
– The Negligent Insider:This type is simply unaware of the dangers associated with sharing login credentials, opening suspicious emails, or visiting malicious websites.
– The Compromised Insider: is someone that has in some way had their credentials compromised. This can happen through a phishing scam, a computer virus, or by sharing their login credentials with the wrong person.
– The Malicious Insider: like a double agent — they work within the organization, but have aspirations to bring harm to the organization.
Here are a few reasons why ActivTrak is an ideal solution for Insider Threat Detection:
– Alarms trigger automated security alerts and reactions. Terminate an unauthorized application, send on-screen notifications, capture screenshots, and watch video playback when the event took place.
– Behavioral data is available on the dashboard within moments of installation. Review reports and screen captures to locate suspicious application usage, website history, and USB activity.
– Gain visibility when a user evokes in-browser Incognito Mode and understand if the user is attempting to evade detection, and why.
– Investigate security breaches and come to a data-supported conclusion about what happened, when it happened, and who was responsible.
– Spot sudden changes in user schedule and passive time, providing additional context to abnormal usage patterns.
– Consult the Risk Level Report to see which users exhibit high-risk behavior and which suspicious activities occur more frequently.
– Check in on your team any time, anywhere from the desktop or the mobile app.
8. Defendify
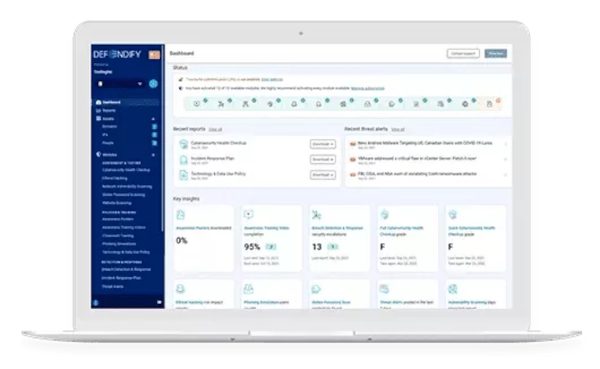
Defendify is designed to meet your growing security needs, Defendify streamlines multiple layers of cybersecurity through a single platform, ongoing guidance, and expert support.
This platform offers:
– A comprehensive, proactive protection
Multiple layers of cybersecurity to continuously protect across people, process, and technology.
– Fast and flexible solutions
Automated and scalable solutions to evolve with you and the ever-changing threat landscape.
– Expert guidance and support
Ongoing, human-powered industry insights and expertise to support your cybersecurity needs.
All-in-one cybersecurity saves time and money. Defendify’s award-winning platform combines multiple layers of cybersecurity protection into one pane of glass through one subscription with one vendor and one budget request. An all-in-one cybersecurity partner can help you streamline your stack, easily augment your staff, and simplify the management and reporting of your cybersecurity health and hygiene.
– All-In-One Cybersecurity:
Maximize cybersecurity protection with multiple layers of security in one platform plus ongoing cybersecurity support and guided expertise.
– Detection & Response:
Neutralize cyberattacks with incident response planning and 24/7 active monitoring and containment by cybersecurity experts.
– Policies & Training:
Promote cybersecurity awareness through ongoing phishing simulations, training and education, and reinforced security policies.
– Assessments & Testing:
Uncover vulnerabilities through ongoing assessments, testing, and scanning across networks, endpoints, applications, and the dark web.
How does this platform work?
Simply enroll anyone on your team you’d like to receive cybersecurity threat alerts and summarized notifications will arrive in their inbox. Administrators always have real-time access to alerts and notifications within the Defendify platform.
While every employee has a responsibility to protect the company against cybersecurity threats, threat alerts are best viewed and managed by IT professionals and management teams. If you don’t have an internal IT resource, that’s when owners or operations managers should receive threat alerts and relay anything of concern internally and to their IT partner (e.g. managed service provider, security system integrator, etc.).
9. Check Point
Threat Intelligence from Check Point provides the best data to identify and prevent all cyber threats that currently or will soon target your organization. Real-time threat intelligence derived from hundreds of millions of sensors worldwide, enriched with AI-based engines and exclusive research data from the Check Point Research Team.
This platform is:
– Practical & Powerful Threat Intelligence: Detects 2,000 attacks daily by unknown threats previously undiscovered.
– Real Time Threat Intelligence: Advanced predictive intelligence engines, data from hundreds of millions of sensors, and cutting-edge research from Check Point Research and external intelligence feed.
– Enabling the Best Zero-Day Protection: Up-to-minute information on the newest attack vectors and hacking techniques.
It has the highest Security Effectiveness Score, Check Point achieved the highest security effectiveness score in the 2019 NSS Labs Breach Prevention System (BPS) group test. Check Point’s Next Generation Firewalls and Advanced Endpoint Security achieved a 100% block rate, and earned a “Recommended” rating. Highlights of Check Point’s results:
– 99.84% overall security effectiveness
– 100% block rate
– 100% malware prevention, email and web
– 100% exploit resistance
– 0% false positives
Pre-emptive User Protections as Humans are the weakest link in the security chain. Pre-emptive user protections eliminate threats before they reach the users regardless of the user activity, browsing or using email.
- Threat extraction delivers clean versions within seconds
- Advanced email protection inspects every element of the email before it reaches the user’s mailbox
- Defends against phishing, social engineering and other email-based threats
Fueled by the Power of ThreatCloud, the Most Powerful Threat Intelligence, real-time threat intelligence derived from hundreds of millions of sensors worldwide, enriched with AI-based engines and exclusive research data from the Check Point Research Team.
AI-Generated Threat Emulation Verdicts leveraging the power of data science to detect the unknown threats with AI engines and rich rule-based engines that process millions of parameters collected from runtime behaviors—reaching a single conclusive AI-generated verdict.
- Deep CPU-level emulation that is resistant to the most evasive attacks
- OS-level inspection
- Malware DNA analysis
10. Cyberint
Cyberint’s Digital Risk Protection and Threat Intelligence solution protects your business from cyber threats beyond the perimeter and alerts if your data or assets are exposed. It protects digital assets, monitors external attack surface and act on threat intelligence.
Gain insights of threats from the ever-growing list of sources, such as open, deep & dark web, chatters, social media, and more for faster and more informed decision-making.
This is how this platform works:
– Collect relevant items: Gather only the most relevant threat intelligence items from the ever-growing list of sources, including open, deep and dark web forums, marketplaces and sites, we’re everywhere that threat actors are.
– Execute complex analysis: Apply machine learning and natural language processing algorithms to determine raw data relevancy and significance for your organization.
– Present and integrate intelligence: Present targeted intelligence to your organization’s security team with the Argos Edge™ web interface. You can also integrate with external systems via web service APIs in real time.
– Understand correlation: Highlight the relationship between entities to create a better image of the attack vector. Connect the dots between IOCs and prioritize the specific actions your organization needs to take.
The advantages are:
– Real-time, targeted and enriched
Cyberint’s Argos Edge provides real-time, targeted Threat Intelligence, collected from thousands of sources, as well as operational threat intelligence collected from numerous feeds to augment that data.
– Advanced, anonymous crawlers and proxies
The targeted intelligence capabilities built into Argos Edge rely on an array of advanced crawlers and proxies which enable data collection from thousands of relevant sources while maintaining anonymity.
– Bypasses human authentication and trust mechanisms
These crawlers can automatically handle and bypass human authentication/trust mechanisms such as CAPTCHA. For special access forums and dark web sites, Cyberint’s team of analyst and researchers create and manage avatars to gain access to these sites.
– Continuously evolving sources and fields
Cyberint constantly adds more feeds to its aggregation engine to provide a holistic view of the customer’s threat landscape, using all available intelligence methodologies.
Conclusion
In this article, we learned about threat intelligence platforms and why organizations rely on them to detect the earliest indications of high-impact events, emerging risks and other business critical information so they can better protect their people, brand and physical and digital assets.





