10 Best Incident Response Software
The incident response softwar are vital in enabling organizations to quickly identify and address cyberattacks, exploits, malware, and other internal and external security threats. also, the tools allow teams to develop workflows, delegate responsibilities, and automate low-level tasks to optimize response time and minimize the impact of security incidents.
Top 10 Software
What is the Best Incident Response Software ?
1- KnowBe4

KnowBe4 is the world’s largest integrated platform for security awareness training combined with simulated phishing attacks. one of product KnowBe4 is Phishing :
You can schedule regular Phishing Security Tests (PST for short) from our large library of more than 10,000 “known-to-work” templates, choose from the community templates section, which were created by admins for admins to share with their peers. You can also create your own custom phishing templates. There are many more features!
The Industry Benchmarking feature lets you compare your organization’s Phish-prone percentage™ with other companies in your industry. See where you stack up! Monitor your employee phish-prone percentages over time and watch how performance from your initial baseline phishing test, after 90 days, and 1 year compares. With regular phishing security tests and security awareness training campaigns, you’ll see how your Human Firewall improves over time helping to reduce risk and improve your IT security defense. You’ll have real-time stats that helps you keep a pulse on how your security awareness program and employees stack up against other companies in your industry. Great intel to share with your management team!
Our Phishing Reply Tracking allows you to track if a user replies to a simulated phishing email and can capture the information sent in the reply. You can also track links clicked by users as well as test and track if users are opening Office attachments and then enabling macros.
In case an employee falls for one of these simulated phishing attacks, you have several options for correction, including instant remedial online training. You can schedule one-shot, weekly, bi-weekly or monthly simulated phishing attacks and immediately see which employees fall for these social engineering attacks. Here is some visible proof the training works over a 12-month period.
In addition, KnowBe4’s no-charge Phish Alert Button reinforces your organization’s security culture, users can report suspicious emails with one click.
When the user clicks the Phish Alert button on a simulated phishing email it’s reported in the Admin Console.
Incident Response gets early phishing alerts from users, creating a network of “sensors”.
Your employee gets instant feedback, which reinforces their training
Now also supports Outlook Mobile!
2- IBM
IBM QRadar SIEM is a highly scalable, enterprise solution that consolidates log source event data from thousands of devices distributed across a network, storing every activity in its database, and then performing immediate correlation and
application of analytics to distinguish real threats from false positives. QRadar SIEM deploys quickly and easily, providing contextual and actionable surveillance across the entire IT infrastructure, helping organizations detect and remediate threats often missed by other security solutions. These threats can include inappropriate use of applications; insider fraud and theft; and advanced, “low and slow” threats easily lost in the “noise” of millions of events.
3. Dynatrace

Dynatrace provides software intelligence to simplify cloud complexity and accelerate digital transformation. With advanced observability, AI, and complete automation, the company’s all-in-one platform provides answers, not just data, about the performance of applications, the underlying infrastructure, and the experience of all users. That’s why many of the world’s largest enterprises trust Dynatrace to modernize and automate cloud operations, release better software faster, and deliver unrivaled digital experiences. The Dynatrace team is an international workforce that inspires each other through collaboration rather than competition. Hard work, drive, helpfulness, and honesty go far—as does a continual drive to reinvent the future.
4. Cynet
Cynet 360 takes on a whole different level than traditional endpoint security offerings, by offering a consolidated solution to all aspects of breach protection through a single interface. Unlike endpoint security solutions that only focus on particular types of threats, Cynet 360 protects your entire internal environment – including hosts, files, users, and the network. The platform converges Endpoint protection and EDR, Network Analytics, User Behavior Analytics, Deception, and Vulnerability Management into a single platform, deployed in minutes, and easy to use for any size organization.
One of the highlights is the platform’s ease-of-use, especially important in a market where security products are frequently challenging to deploy and navigate. The platform interface takes the capabilities needed by security professionals and presents them in a way that is more intuitive, making both the implementation process and product management more user-friendly. As it provides multiple capabilities, there’s no longer the need for multiple security product configurations, and makes the job easier for the personnel tasked with security management, even if it is an IT person and not a dedicated security professional.
Without additional cost, Cynet 360 offers the services of CyOps. Their team of security experts who are online 24/7 for alerting about threats, proactive threat hunting, and assisting in incident response.
5. DATADOG

Datadog is a monitoring and analytics tool for information technology (IT) and DevOps teams that can be used to determine performance metrics as well as event monitoring for infrastructure and cloud services. The software can monitor services such as servers, databases and tools.
The features that Datadog offers include:
– Provides an IT/DevOps team with a single view of their infrastructure (including servers, apps, metrics and other services).
– Customizable dashboards.
– Alerts based on critical issues.
– Support for over 250 product integrations.
– Automatically collects and analyzes logs, latency and error rates.
– Allows for access to the API.
Supports applications written in languages such as Java, Paytnon, PHP, .NET, Go, Node and Ruby.
6. Sumologic
Sumo Logic is a pioneer of continuous intelligence, a new category of software, which enables organizations of all sizes to address the data challenges and opportunities presented by digital transformation. Its mission is to empower digital businesses by providing real-time machine data analytics that customers can understand and act on. Companies such as Alaska Airlines, Major League Baseball, Netflix, and Samsung rely on Sumo Logic to build, run, and secure their modern applications and cloud infrastructures. The ideal team member takes calculated risks, learns from their mistakes, and knows how to iterate and do better each time. They’re also hardworking and operate with integrity when working with clients and colleagues.
7. LogRhythm SIEM

LogRhythm can help you tell a cohesive story around user and host data, making it easier to gain proper insight needed to remediate security incidents faster as SIEM.
While security information and event management (SIEM) solutions have been around for over a decade, and have evolved significantly over that time, the core functionality still acts as the most effective foundation for any organization’s technology stack.
At its most fundamental level, a SIEM solution enables an organization to centrally collect data across its entire network environment to gain real-time visibility into activity that may potentially introduce risk to the organization.
Using SIEM technology to achieve visibility into network activity helps organizations address issues before they become a significant financial risk. It also helps operations better manage company assets.
The SIEM essentials
Log management: Collect, normalize, and aggregate log data to deliver efficient data access and management
Real-time monitoring: Observe activity at the exact moment it occurs within your network environment
Incident investigation: Search and drill down on logs to further investigate a potential incident
8. RAPID 7
Rapid7 provides analytics solutions for security and information (IT) operations.
It’s vulnerability management solutions include InsightVM and Nexpose, which enables customers to assess and remediate their overall exposure to cyber risk, AppSpider, an application security testing solution and Metasploit, a penetration testing software solution.
The company’s incident detection and response solutions or SIEM comprise InsightIDR, an insight platform-based solution. In addition, it provides Logentries, a cloud-based solution for collecting, searching, visualising, and analysing log data, as well as enabling organisations to store and search data.
Furthermore, the company provides security advisory services, such as cyber security maturity assessment, incident response program development, penetration testing, security program development, Virtual CISO, IoT security, and threat modelling services.
9. Logpoint
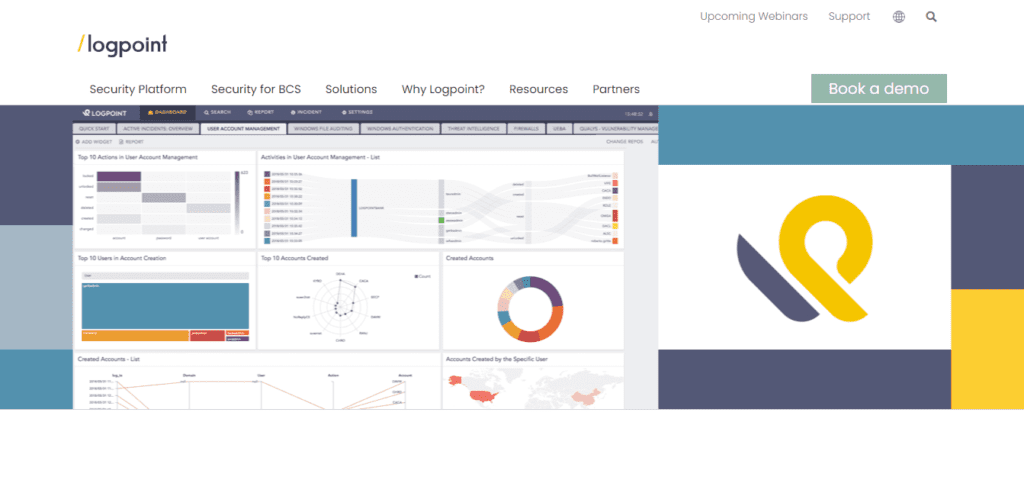
LogPoint is the creator of a reliable, innovative cybersecurity operations platform — empowering organisations worldwide to thrive in a world of evolving threats.
By combining sophisticated technology and a profound understanding of customer challenges, LogPoint bolsters security teams’ capabilities while helping them combat current and future threats. LogPoint offers SIEM, UEBA, and SOAR technologies in a complete platform that efficiently detects threats, minimises false positives, autonomously prioritises risks, responds to incidents, and much more.
10. Blumira
Blumira is a cybersecurity provider that helps SMB and mid-market companies detect and respond to security threats, while meeting compliance and cyber insurance requirements.
Originally founded due to frustration with overly complex SIEM platforms, Blumira focuses on providing accessible solutions for resource-strapped IT and security teams. We proactively update our platform to keep up with the latest vulnerabilities and attack methods, doing all the heavy lifting for our customers.
We’ve spent decades defending networks, including deep experience in ethical hacking that has helped us develop an effective platform that SMBs can actually use to identify and respond to real threats. With a customer satisfaction score at 100%, we’re truly committed to customer security success.





